SSL/TLS configuration
Depending on the environment, Conduktor might need to access external services like Kafka clusters, SSO servers, database, or object storage that require a custom certificate for SSL/TLS communication.
The following table gives you an overview of what's currently supported and the methods to configure it:
- From the UI (recommended): From Conduktor Console, you can manage your certificates on a dedicated screen. You can also configure SSL authentication from the broker setup wizard.
- Volume mount: This method is only required if you have LDAPS. Do not use it for Kafka or Kafka components.
| Kafka Clusters | Schema Registry / Kafka Connect | LDAPS, OIDC | |
|---|---|---|---|
| SSL to secure data in transit | ✅ UI | ✅ UI | ✅ UI |
| SSL to authenticate the client | ✅ UI | ✅ UI | 🚫 Not supported |
Jump to:
- Using the Conduktor Certificate Store
- Recommended for Kafka, Kafka Connect and Schema Registry connections
- Mounting Custom Truststore
- Recommended for SSO, DB or other external services requiring SSL/TLS communication
- Client Certificate Authentication
- Recommended for mTLS; import your keystore file
Using the Conduktor Certificate Store
You can manage custom certificates for Kafka, Kafka Connect and Schema Registry through the Console UI. This enables you to import and parse the certificates as text or files. The supported file formats are:
.crt.pem.jks.p12
Uploading certificates in the cluster configuration screen
Assuming you have appropriate permissions, you can add cluster configurations from within Admin. When you add the bootstrap server to your configuration, a check will be made to validate if the certificate is issued by a valid authority.
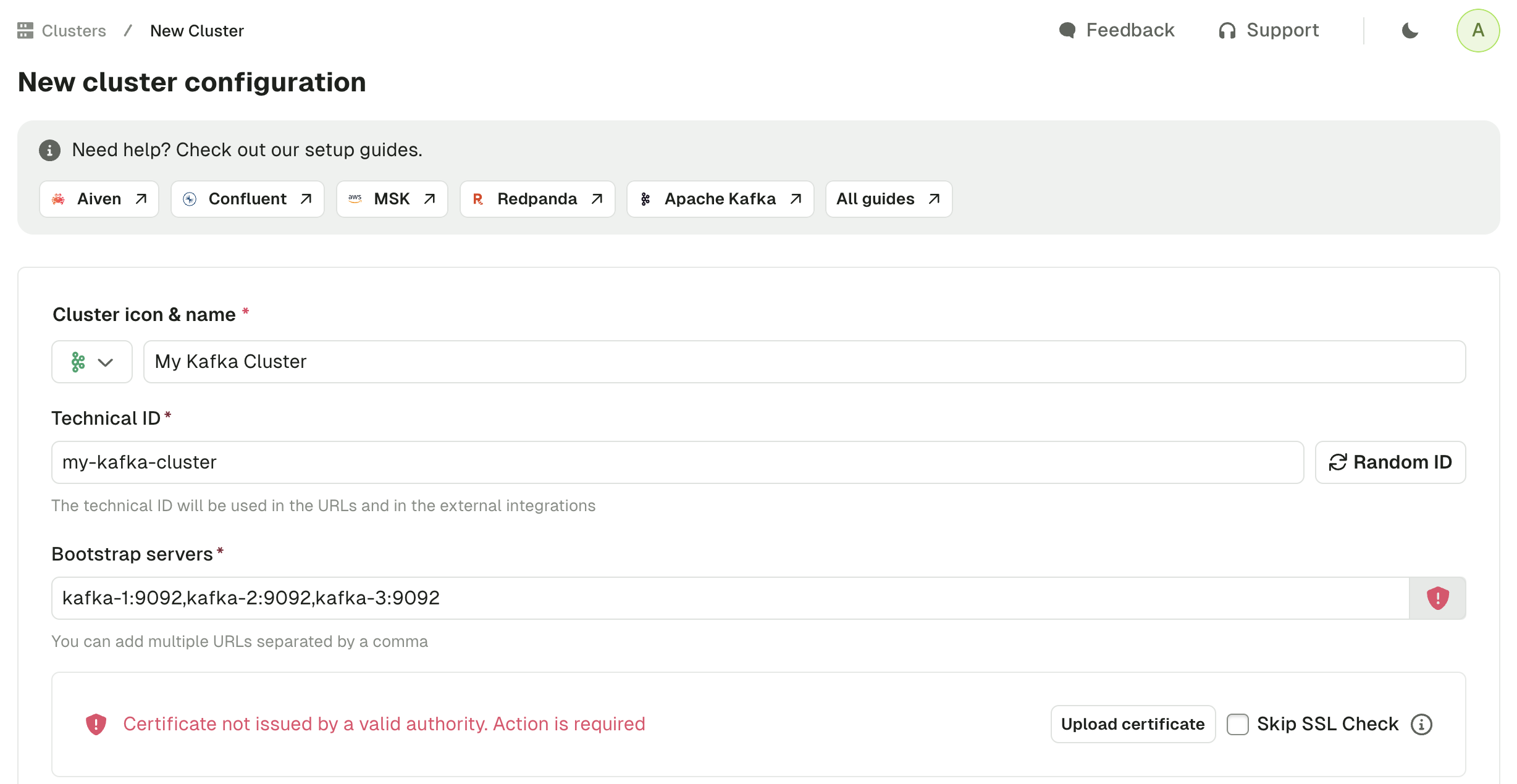
If the response indicates the certificate is not issued by a valid authority, you have two options:
- Skip SSL Check: This will skip validation of the SSL certificate on your server. This is an easy option for development environments with self-signed certificates
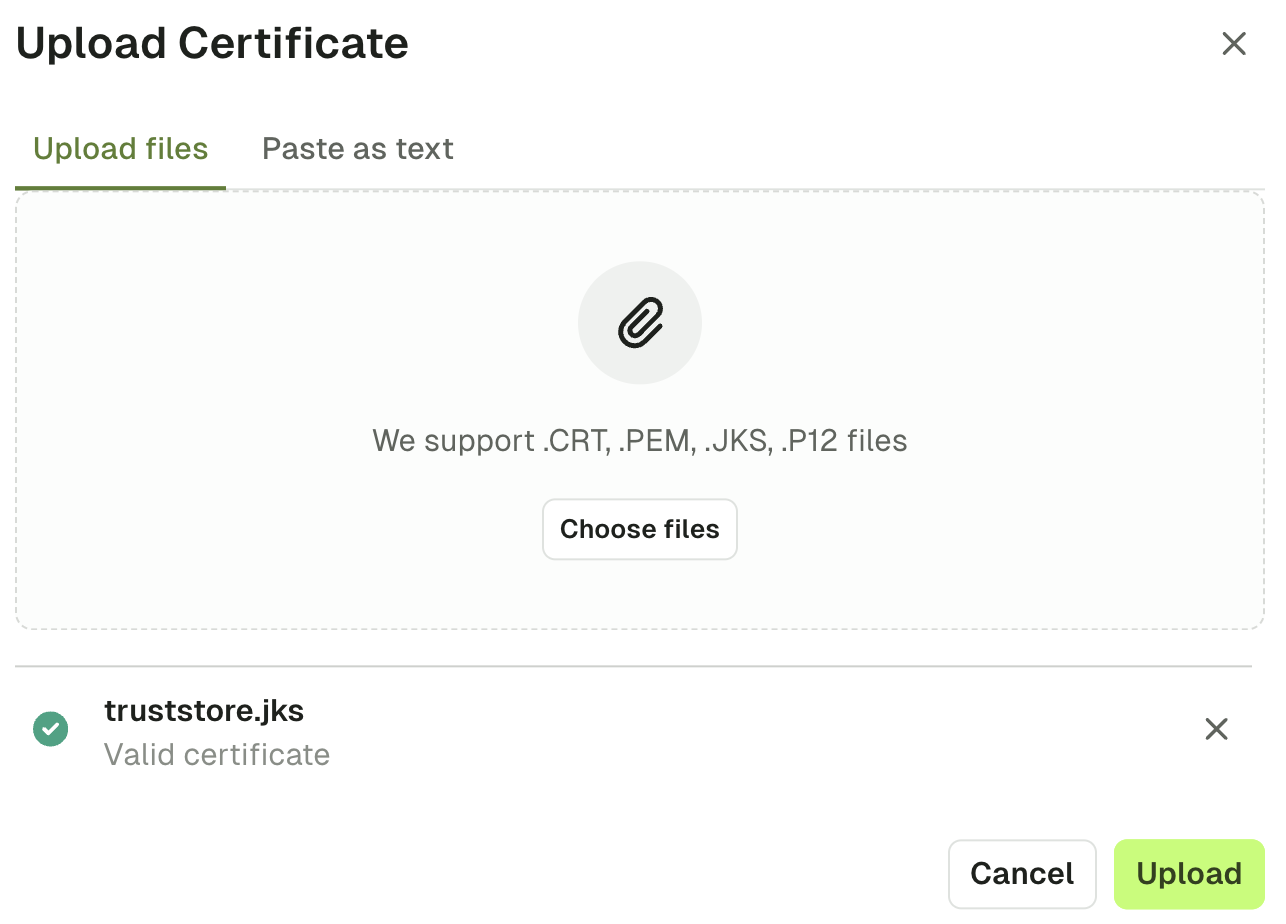
- Upload Certificate: This option will enable you to upload the certificate (
.crt,.pem,.jksor.p12files), or paste the certificate as text
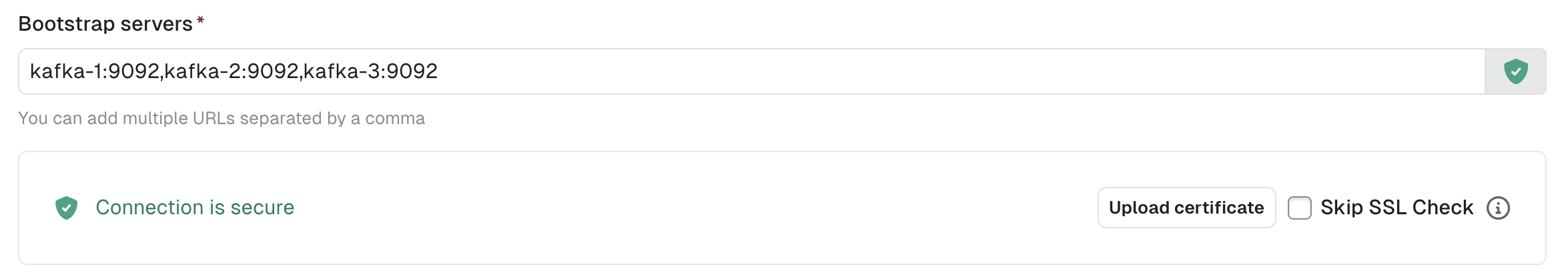
Upon uploading the certificate, you should then see the green icon indicating the connection is secure.
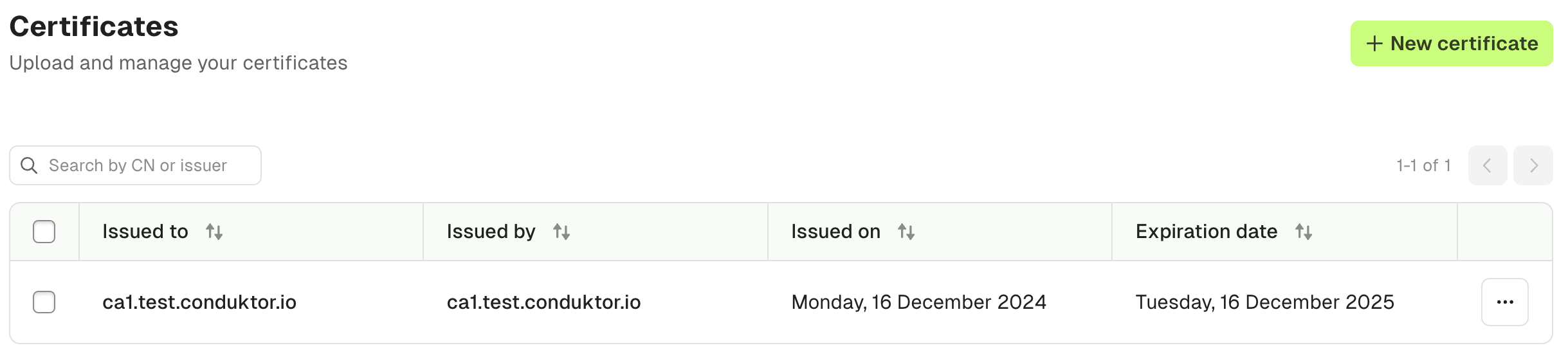
Adding truststores in the dedicated certificates screen
Provided you have permissions, you can also manage organization truststores via the Certificates tab within Settings.
Simply add all of your certificates by uploading them or pasting them as text. In doing this, the SSL context will be derived when you configure Kafka, Kafka Connect and Schema Registry connections.
Mounting Custom Truststore
Conduktor supports SSL/TLS connections using Java Truststore. The below details how to mount a custom truststore when starting Conduktor.
Create TrustStore (JKS) from certificate in PEM format
If you already have a truststore, you can ignore this step.
For that, you need a keytool program that is usually packaged on JDK distributions and a certificate in PEM format (.pem or .crt).
keytool \
-importcert \
-noprompt \
-trustcacerts \
-keystore ./truststore.jks \ # Output truststore jks file
-alias "my-domain.com" \ # Certificate alias inside the truststore (usually the certificate subject)
-file ./my-certificate-file.pem \ # Input certificate file
-storepass changeit \ # Truststore password
-storetype JKS
Configure custom truststore on Conduktor Console
For that we need to mount the truststore file into the conduktor-console container and pass the correct environment variables for locating truststore file inside the container and password if needed.
Assuming that truststore file is named truststore.jks with password changeit.
We mount truststore file into /opt/conduktor/certs/truststore.jks inside the container.
If run from docker :
docker run --rm \
--mount "type=bind,source=$PWD/truststore.jks,target=/opt/conduktor/certs/truststore.jks" \
-e CDK_SSL_TRUSTSTORE_PATH="/opt/conduktor/certs/truststore.jks" \
-e CDK_SSL_TRUSTSTORE_PASSWORD="changeit" \
conduktor/conduktor-console
From docker-compose :
services:
conduktor-console:
image: conduktor/conduktor-console
ports:
- 8080:8080
volumes:
- type: bind
source: ./truststore.jks
target: /opt/conduktor/certs/truststore.jks
read_only: true
environment:
CDK_SSL_TRUSTSTORE_PATH: '/opt/conduktor/certs/truststore.jks'
CDK_SSL_TRUSTSTORE_PASSWORD: 'changeit'
Client Certificate Authentication
This mechanism uses TLS protocol to authenticate the client. Other names include:
- Mutual SSL, Mutual TLS, mTLS
- Two-Way SSL, SSL Certificate Authentication
- Digital Certificate Authentication, Public Key Infrastructure (PKI) Authentication
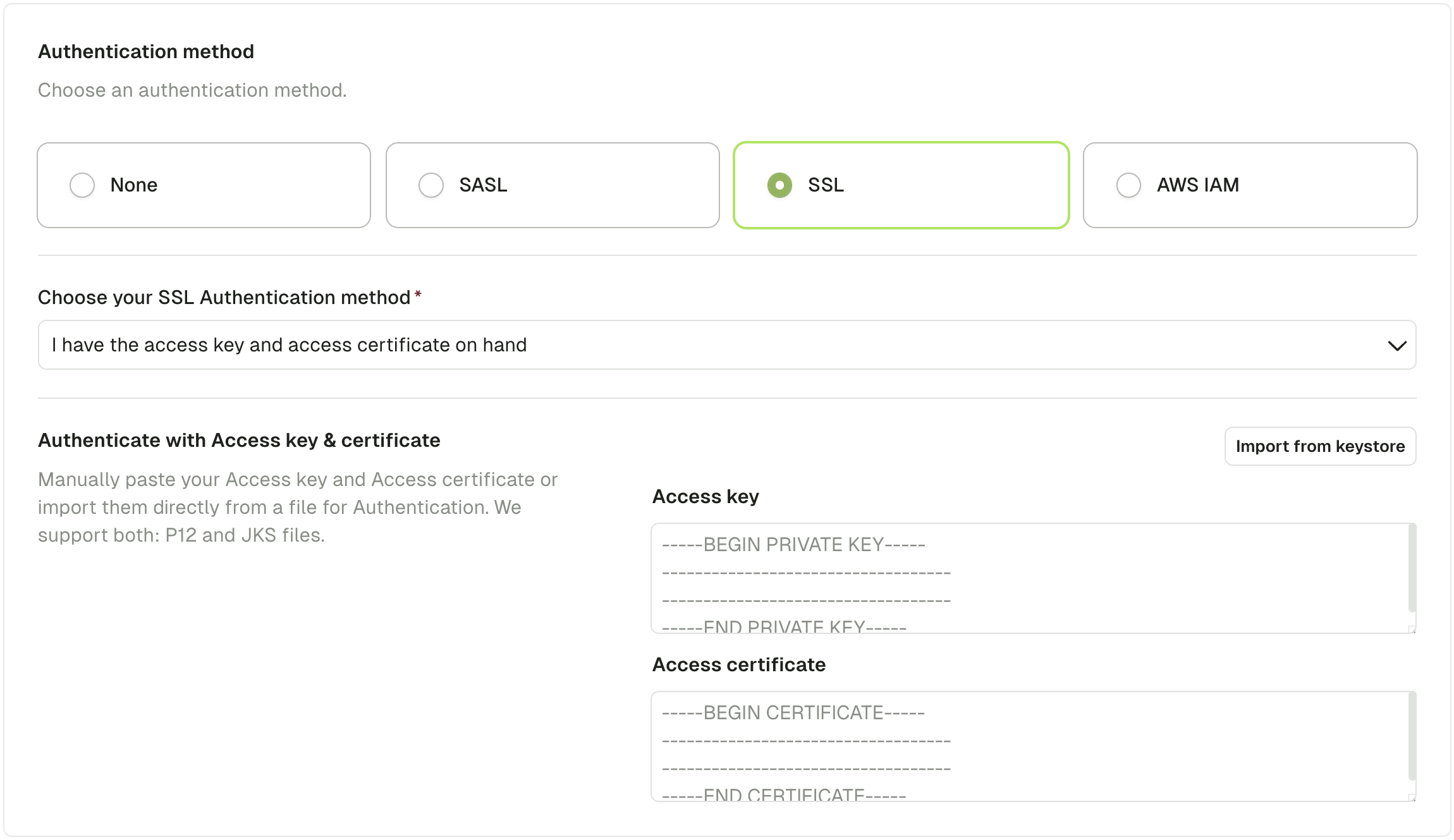
Using the UI (keystore method)
Your Kafka Admin or your Kafka Provider gave you a keystore file (.jks or .p12 format).
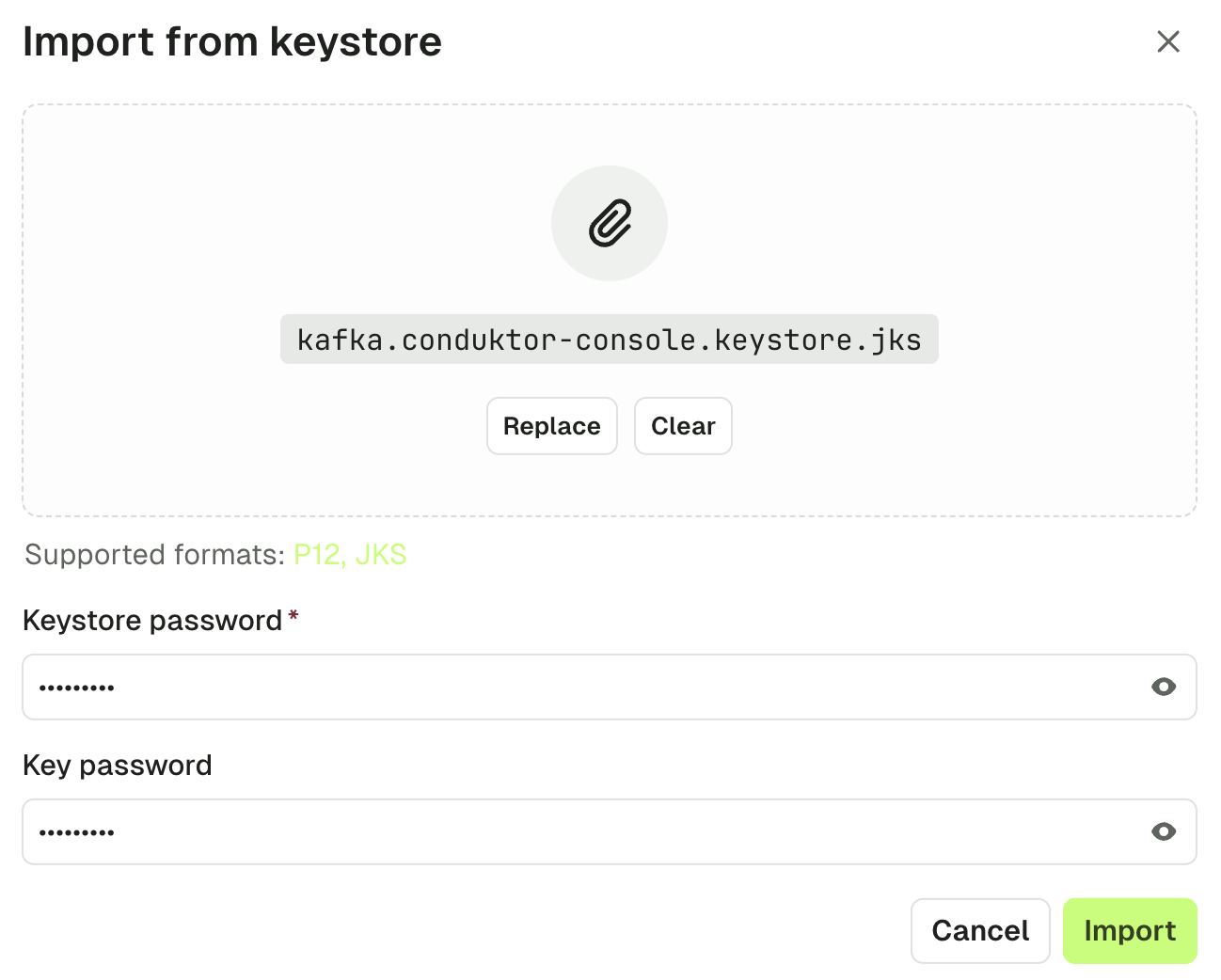
Click the "Import from keystore" button to select a keystore file from your filesystem.
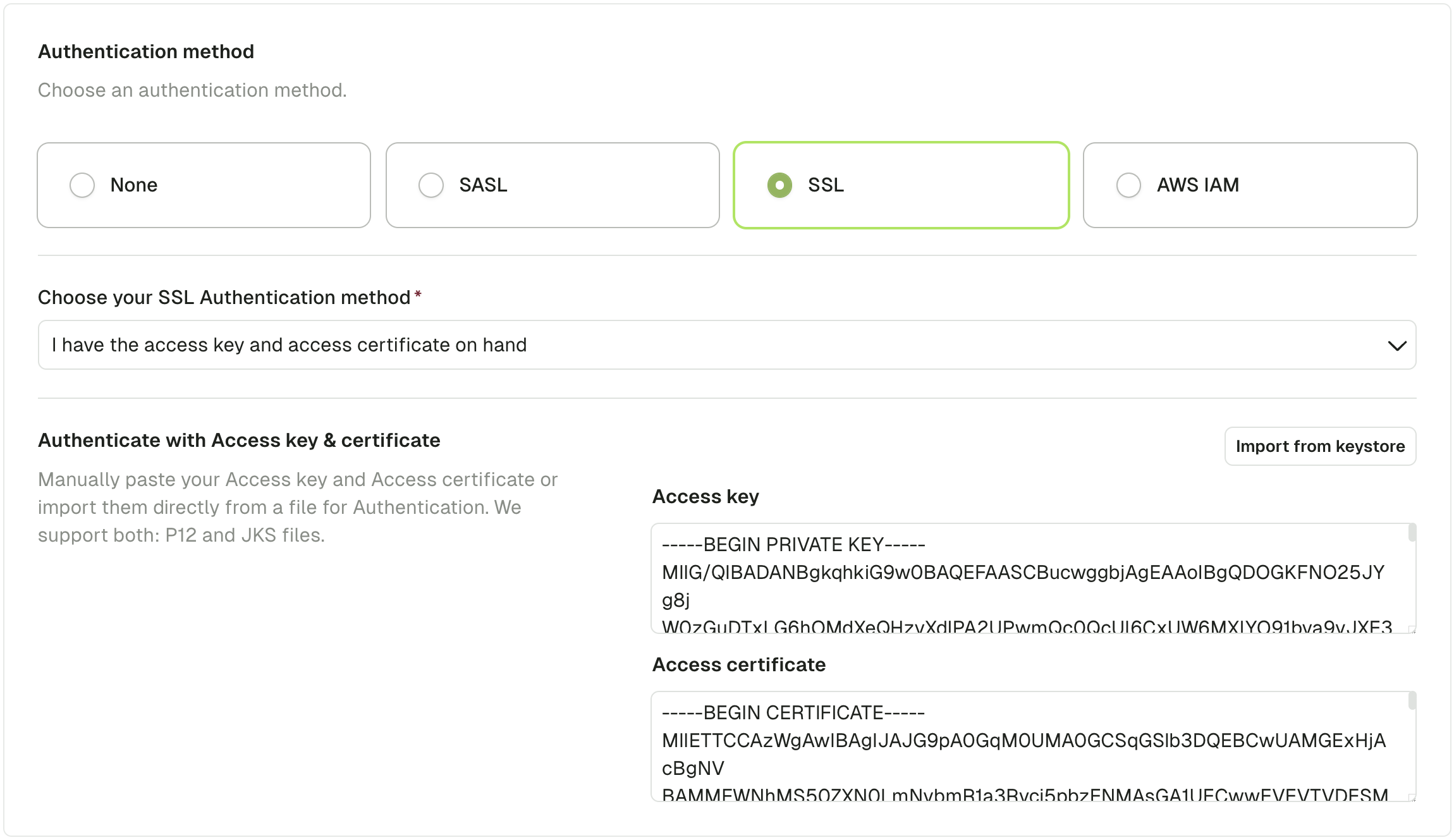
Fill in the required keystore password and key password and click "Import".
You'll get back to the cluster screen with the content of your keystore extracted into Access key and Access certificate.
Using the UI (Access key & Access certificate method)
Your Kafka Admin or your Kafka Provider gave you 2 files for authentication.
- An Access key (
.keyfile) - An Access certificate (
.pemor.crtfile)
Here's an example with Aiven:
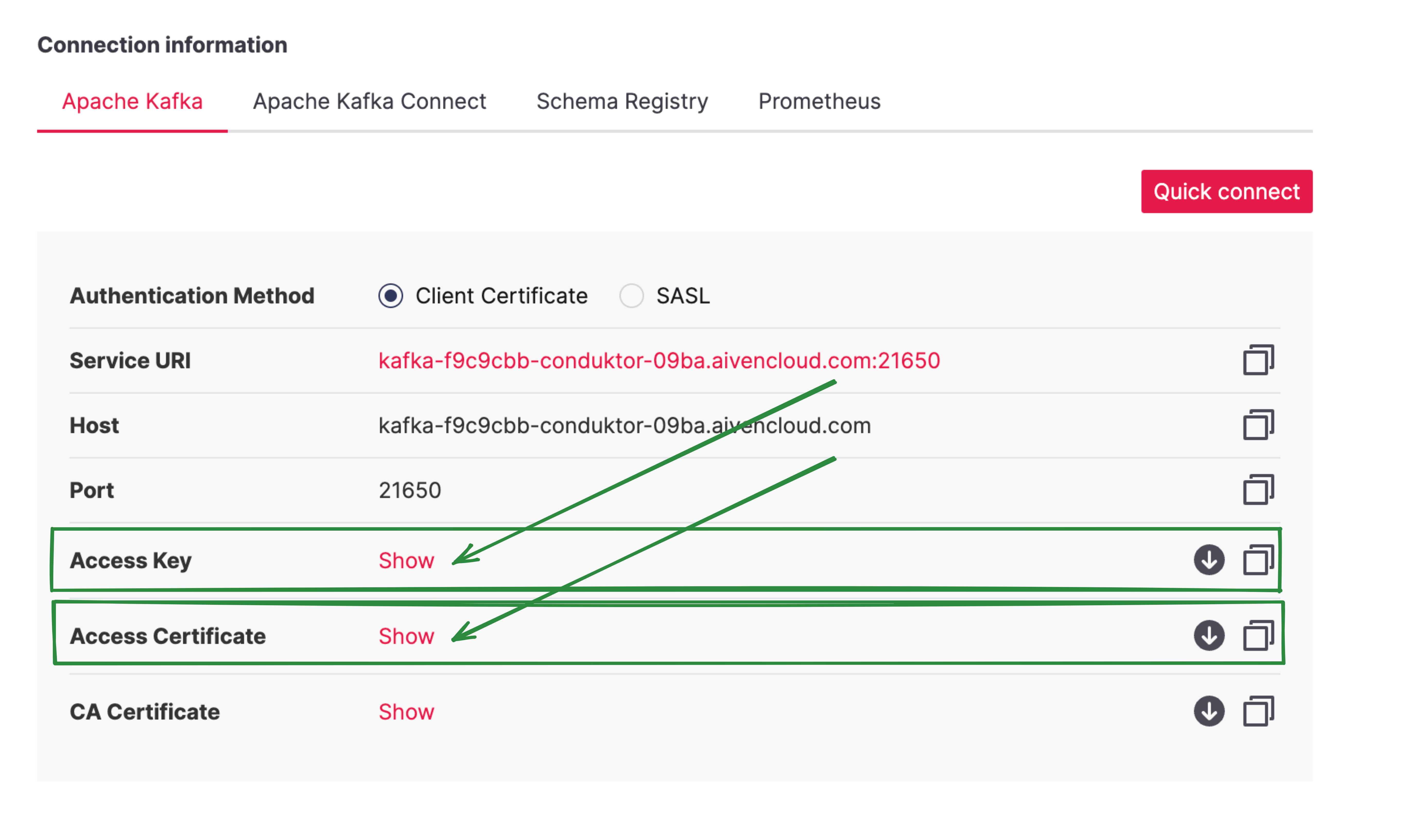
You can paste the 2 file's contents into Conduktor, or alternatively import from keystore as detailed in the previous section.
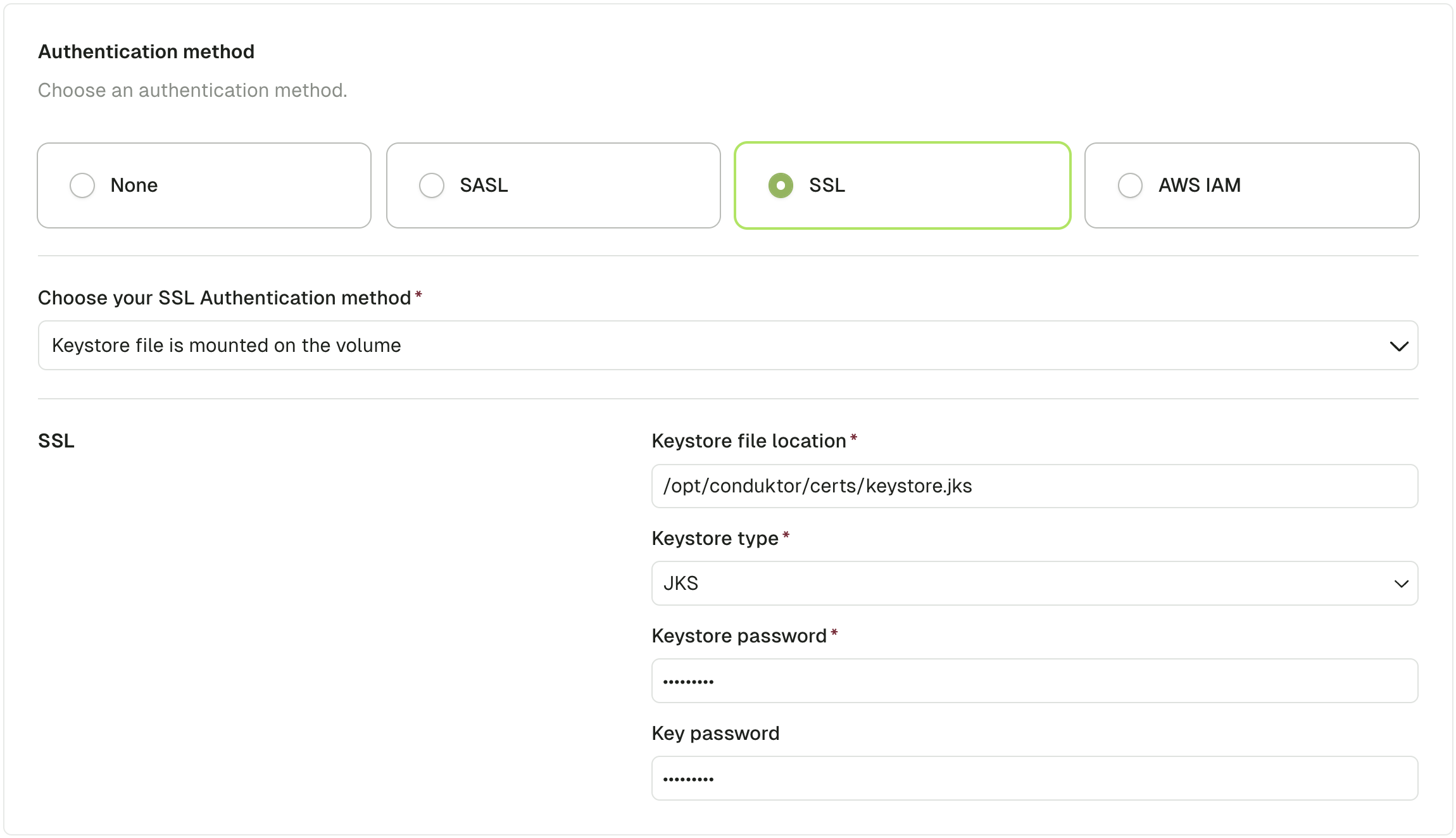
Using Volume Mount (Alternate method)
You can mount the keystore file in 'conduktor-console' image:
services:
conduktor-console:
image: conduktor/conduktor-console
ports:
- 8080:8080
volumes:
- type: bind
source: ./keystore.jks
target: /opt/conduktor/certs/keystore.jks
read_only: true
Then from the UI, choose the SSL Authentication method "Keystore file is mounted on the volume" and fill in the required fields