Overview
To add, update, and delete Kafka cluster configurations, go to Settings > Clusters. By default, only users belonging to the Admin group or having theCan manage Cluster configurations permission will be able to view and manage the clusters.
Network requirements
Console connects to Kafka clusters using the Apache Kafka Java client library. It uses standard Kafka client connections with the bootstrap servers you provide in the cluster configuration. Console requires the same network access to Kafka brokers as any standard Kafka client application.Connect to a Conduktor Gateway cluster
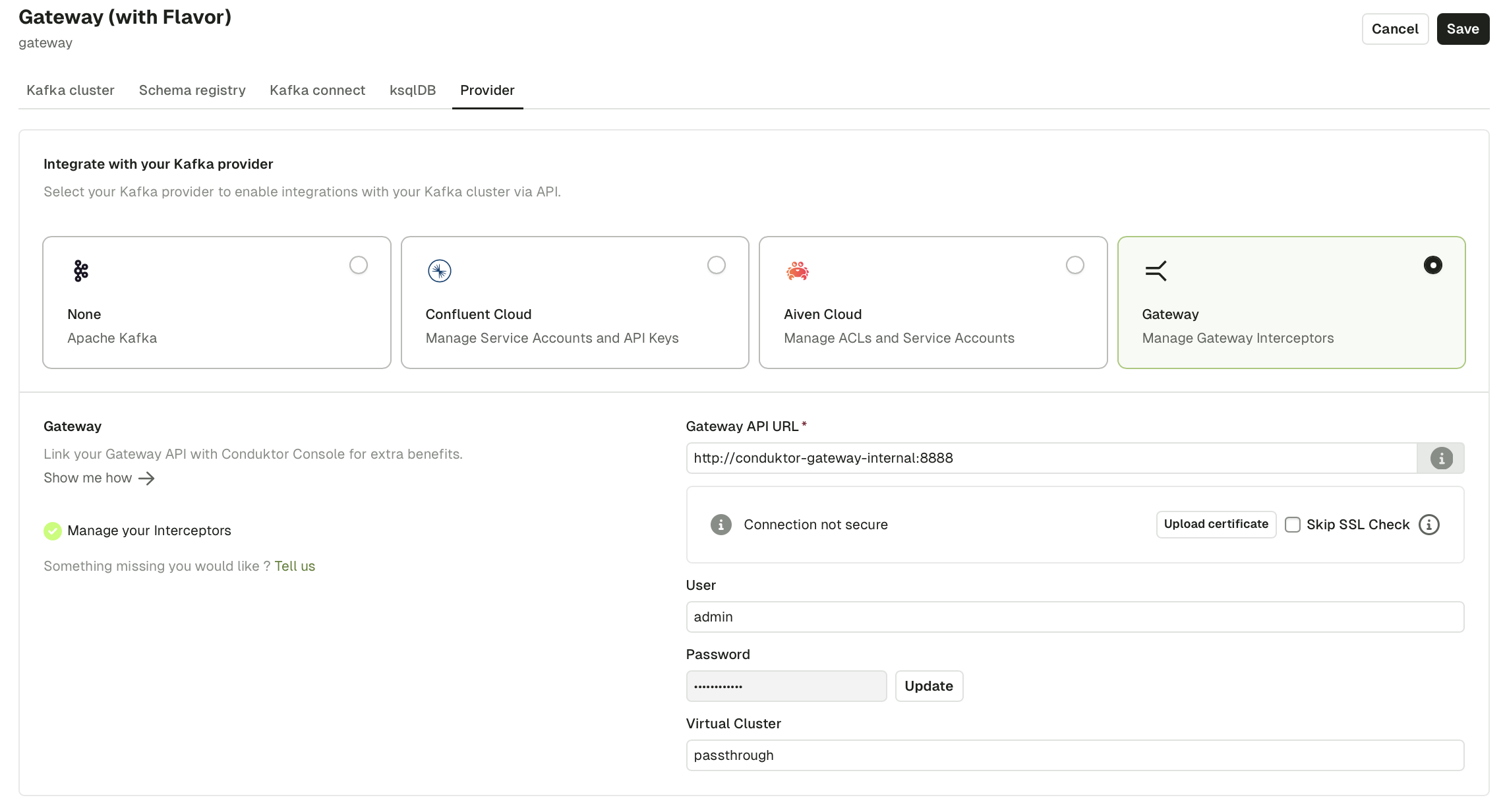
Connect Conduktor Console to a Conduktor Gateway cluster the same way you would connect to any Kafka cluster by providing the Gateway bootstrap servers and security configurations. Console will simply act as a Kafka client connecting to Gateway. The security protocol must match theGATEWAY_SECURITY_PROTOCOL defined in your Gateway configuration.
To enable Gateway integration and access Interceptors, Chargeback with Gateway or Partner Zones, select the Gateway provider and enter your Gateway API key and secret.
Connect to a secure Kafka cluster
Console uses the Apache Kafka Java Client configuration properties . To connect to a secure Kafka cluster, specify the values from yourconfig.properties file:
Connect to a Confluent Cloud cluster
- In your Confluent cluster dashboard, go to Data integration > Clients
- Select Java as the language
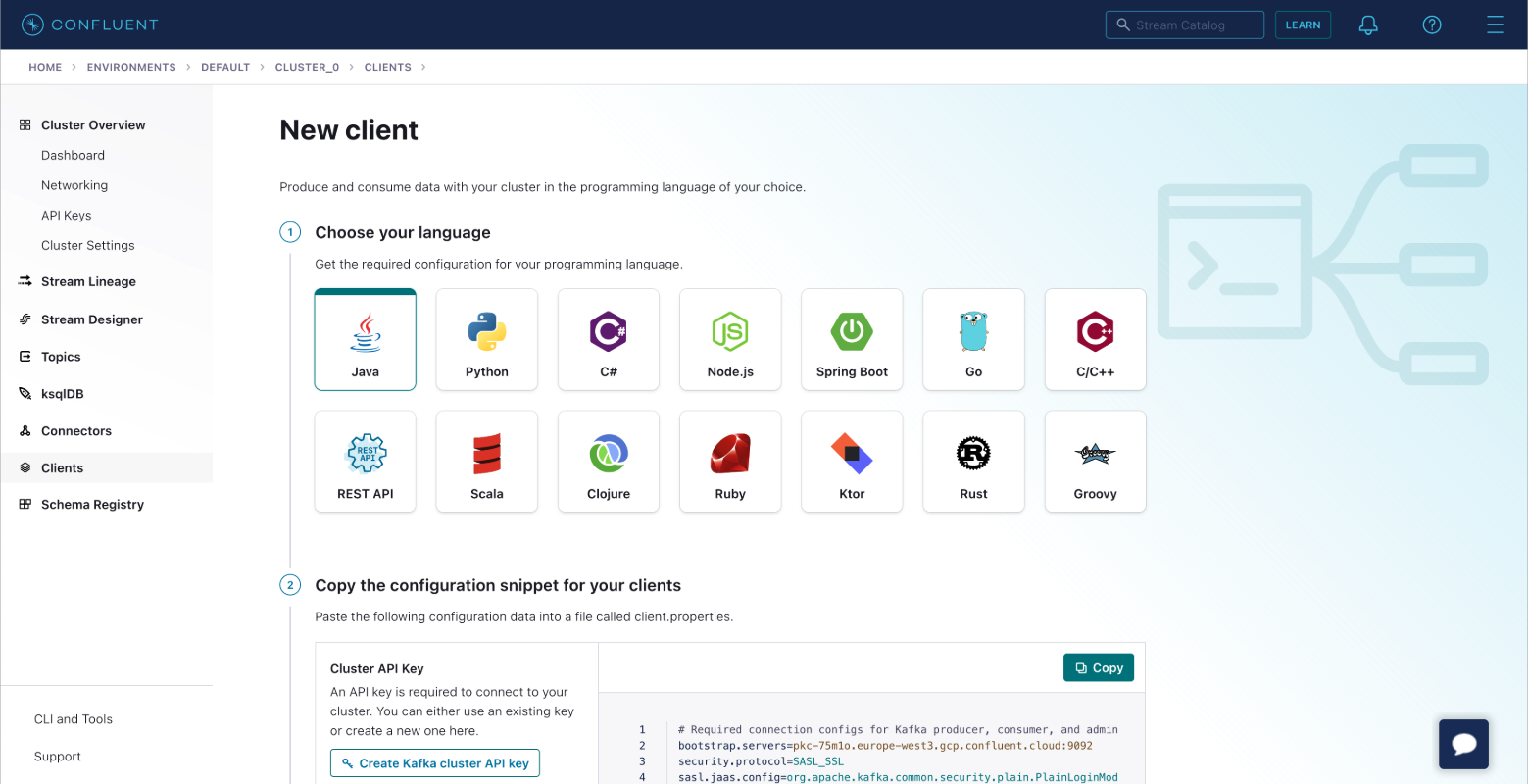
- Create a Kafka cluster API key. Optionally, create a Schema Registry API Key if using Schema Registry
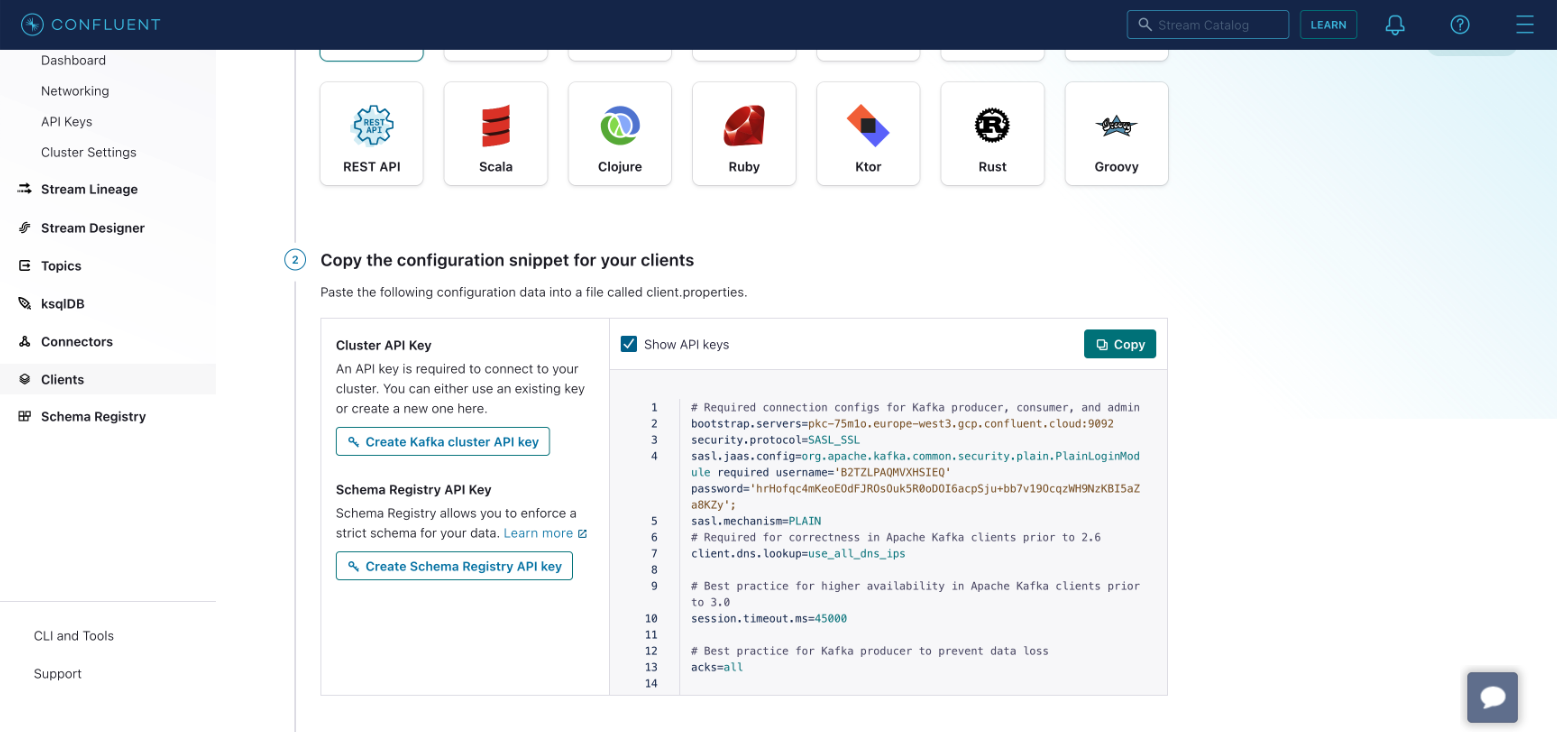
- Copy the configuration to your clipboard.
- In Console, add the bootstrap servers and paste the configuration as advanced properties.
- Test the connection. A green Connected label appears on success.
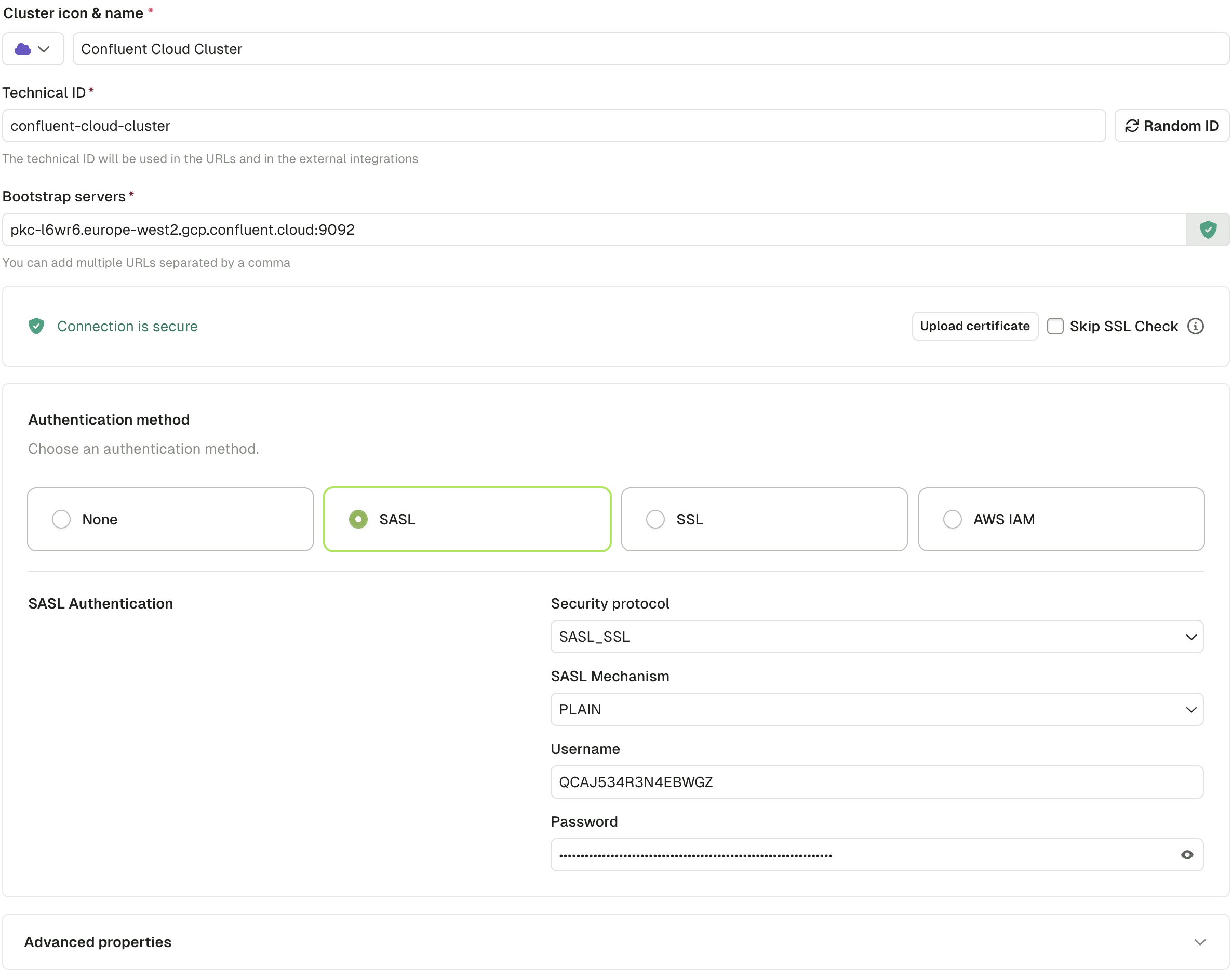
- Click Create Configuration to save
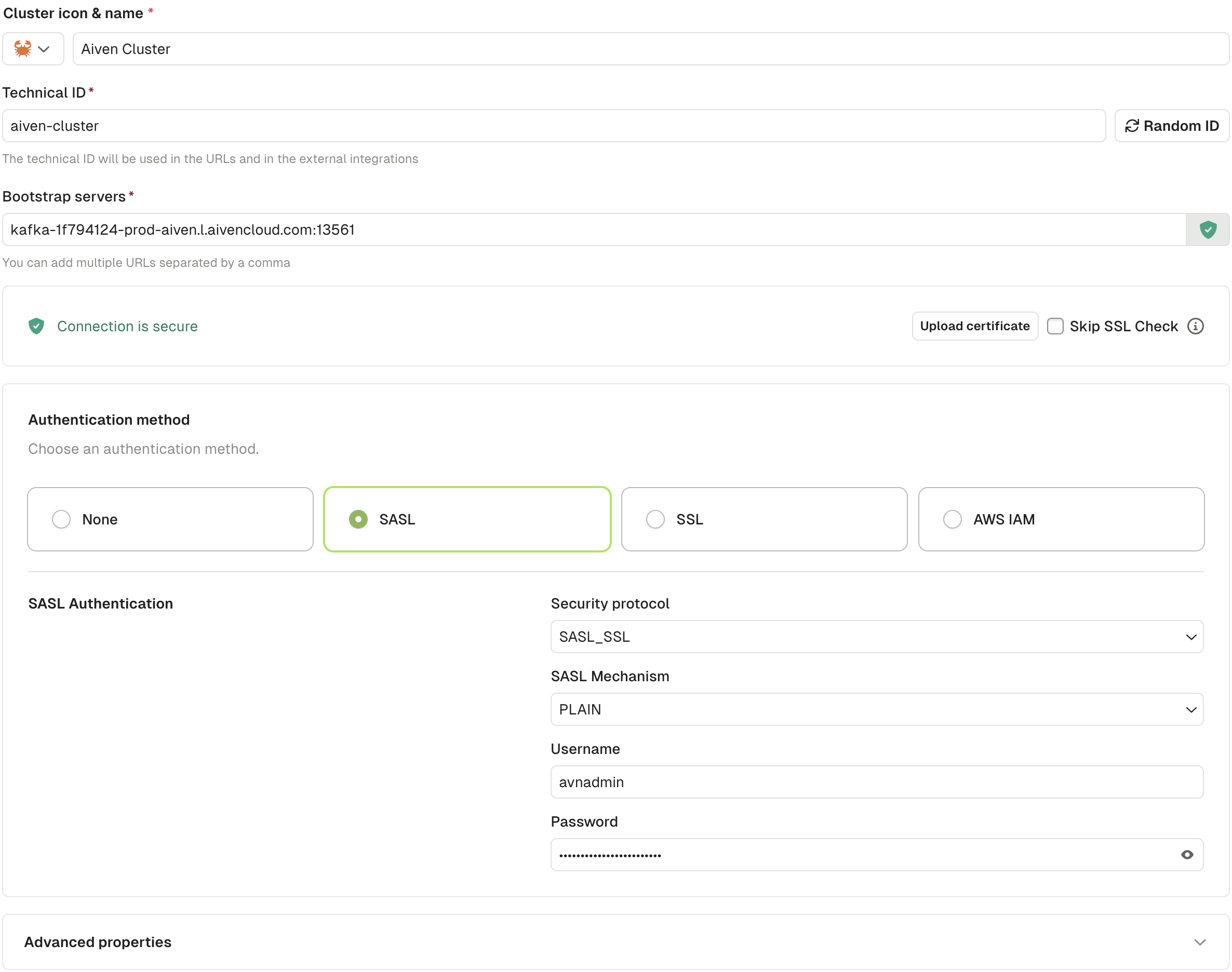
Connect to an Aiven cluster
Choose one of the following authentication methods:SSL authentication
Provide the Access Key, Access Certificate, and CA Certificate from your Aiven console. The Service URI is your bootstrap server.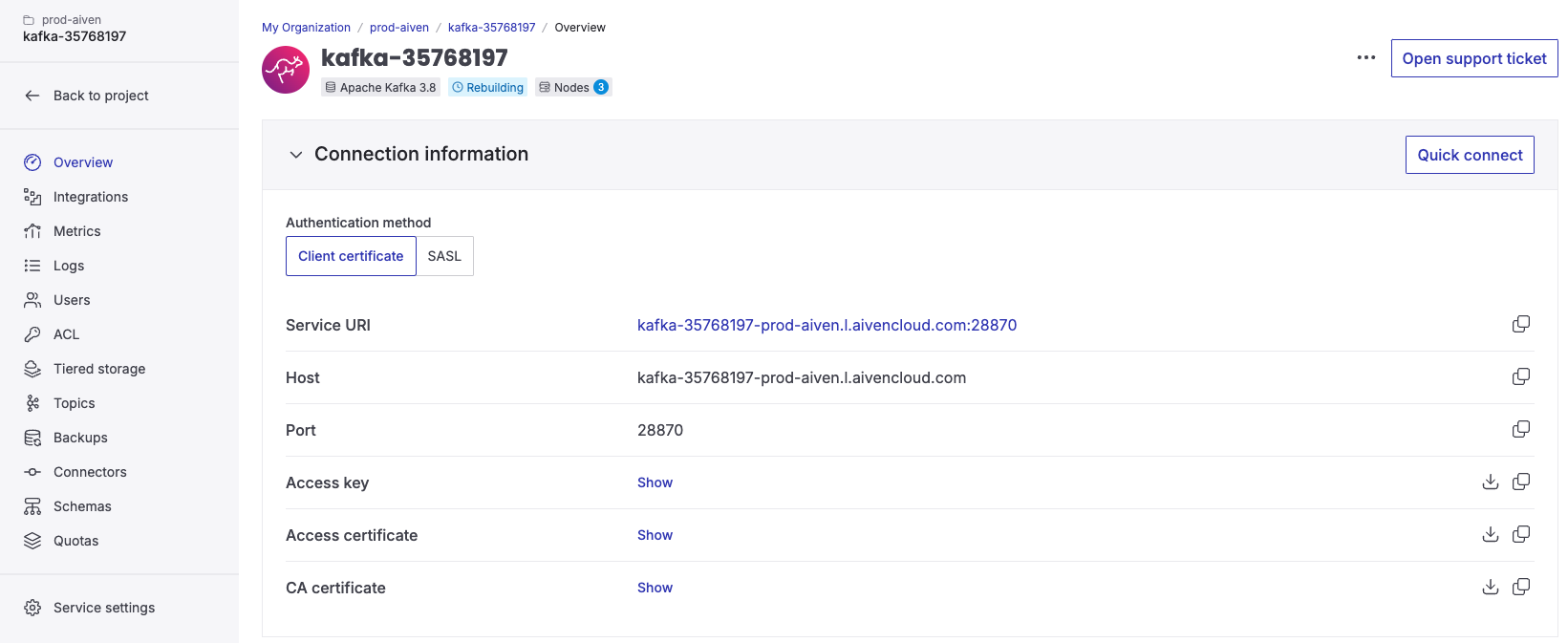
- Enter the bootstrap server
- Upload the CA certificate
- Select SSL as the authentication method
- Paste the Access Key and Access Certificate
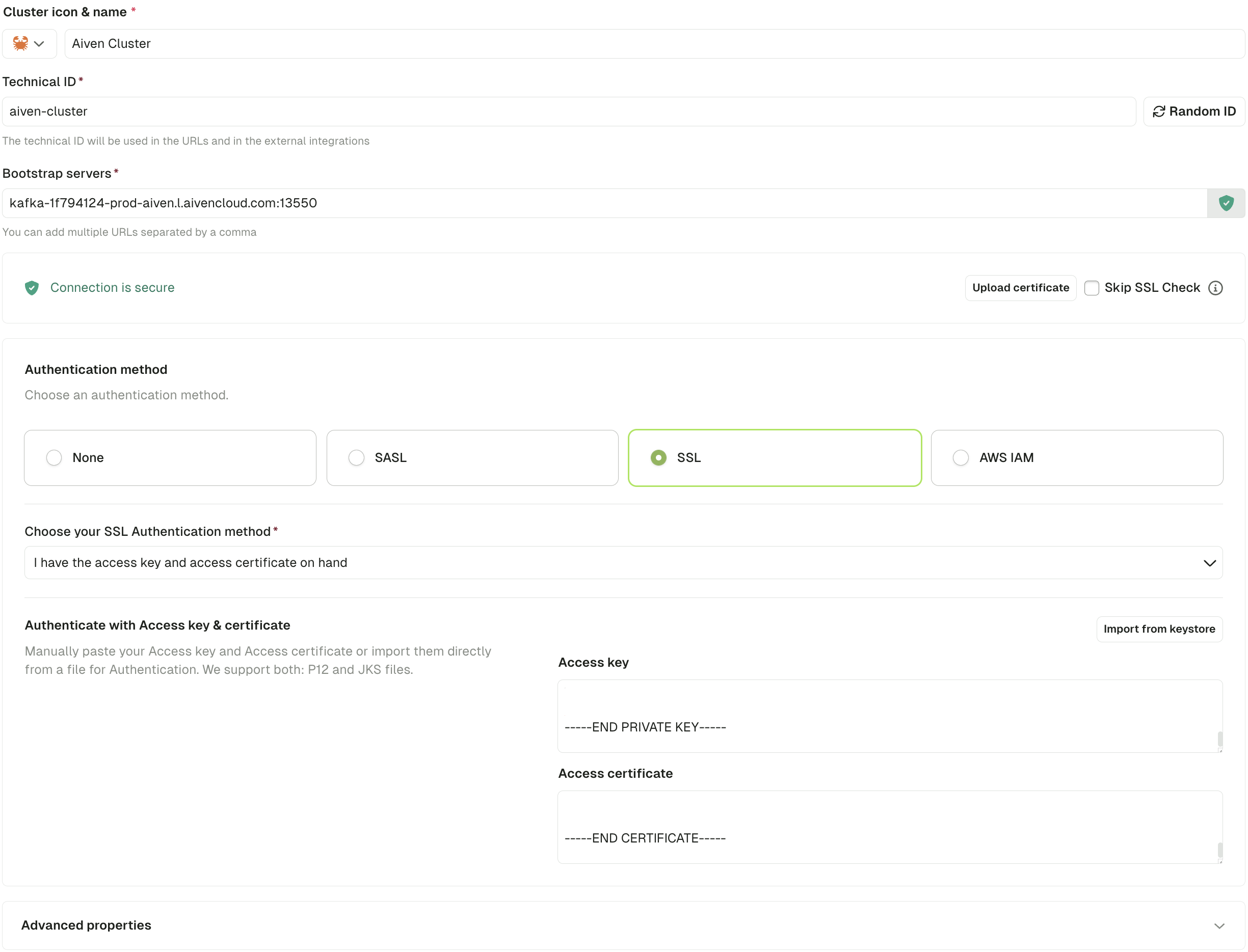
SASL_SSL authentication
Provide the Service URI (bootstrap server), User, and Password from your Aiven console.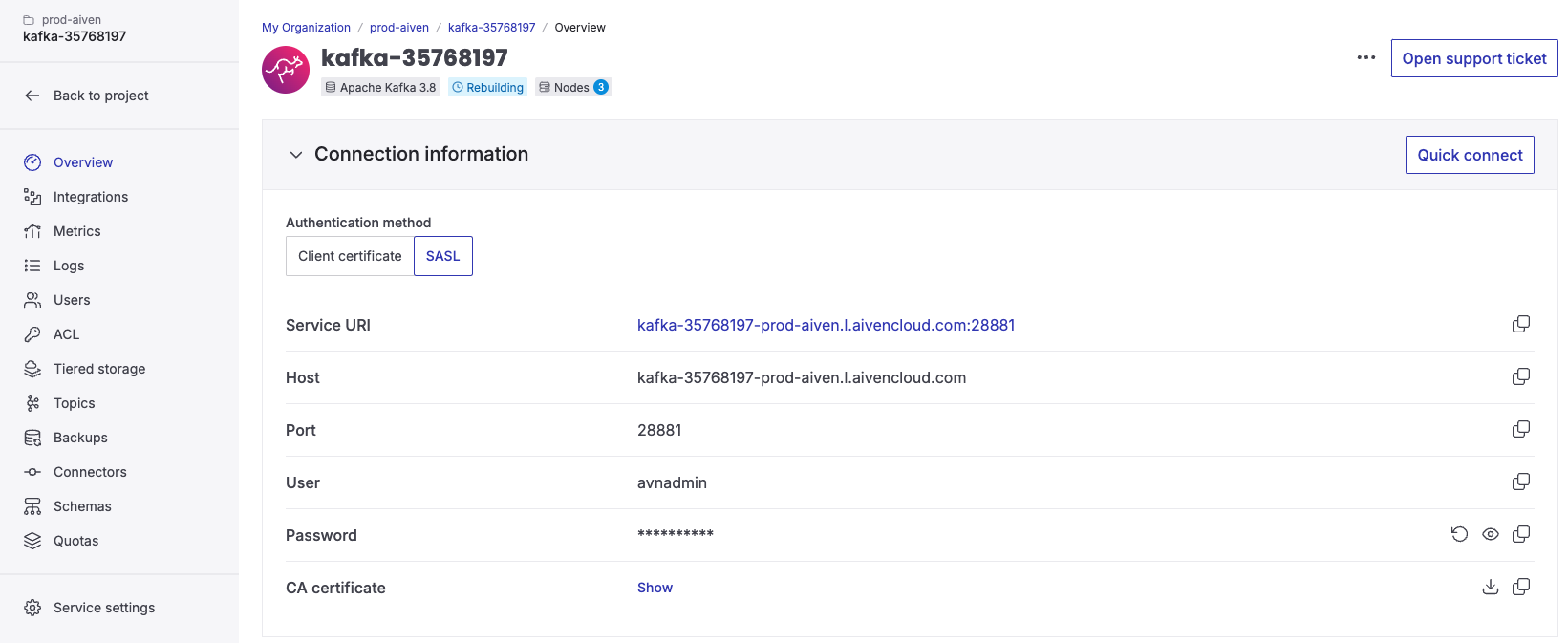
Connect to an AWS MSK cluster
- Create an IAM user:
- Attach permissions to the IAM user:
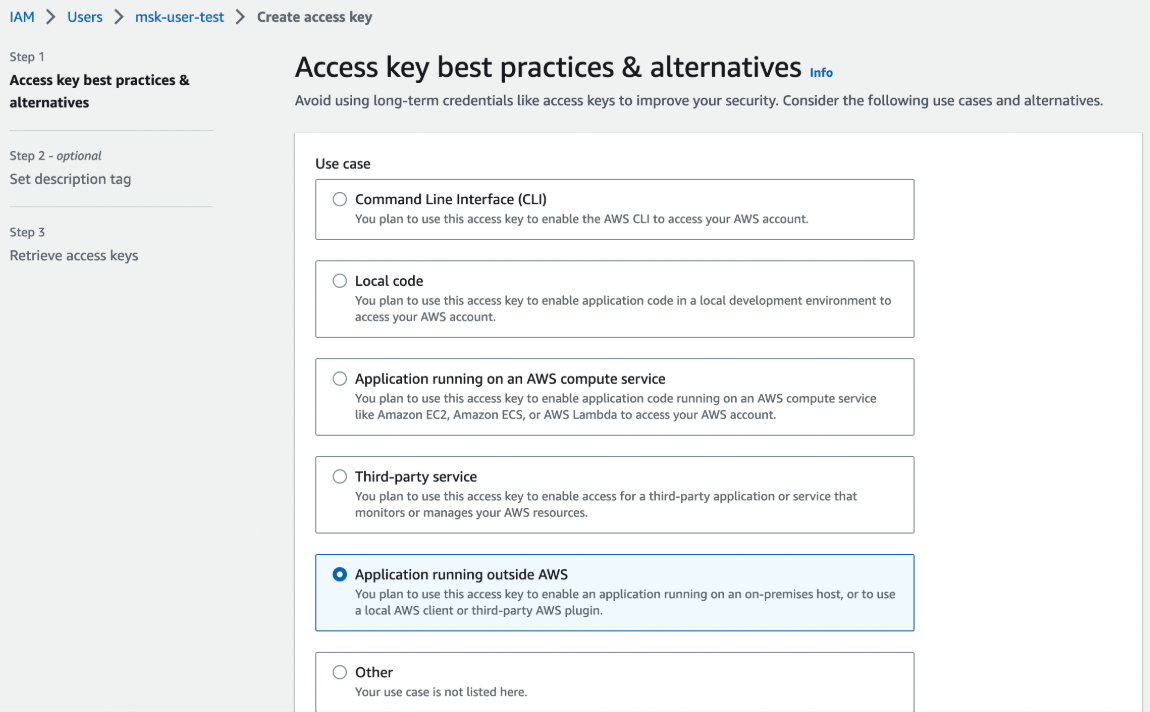
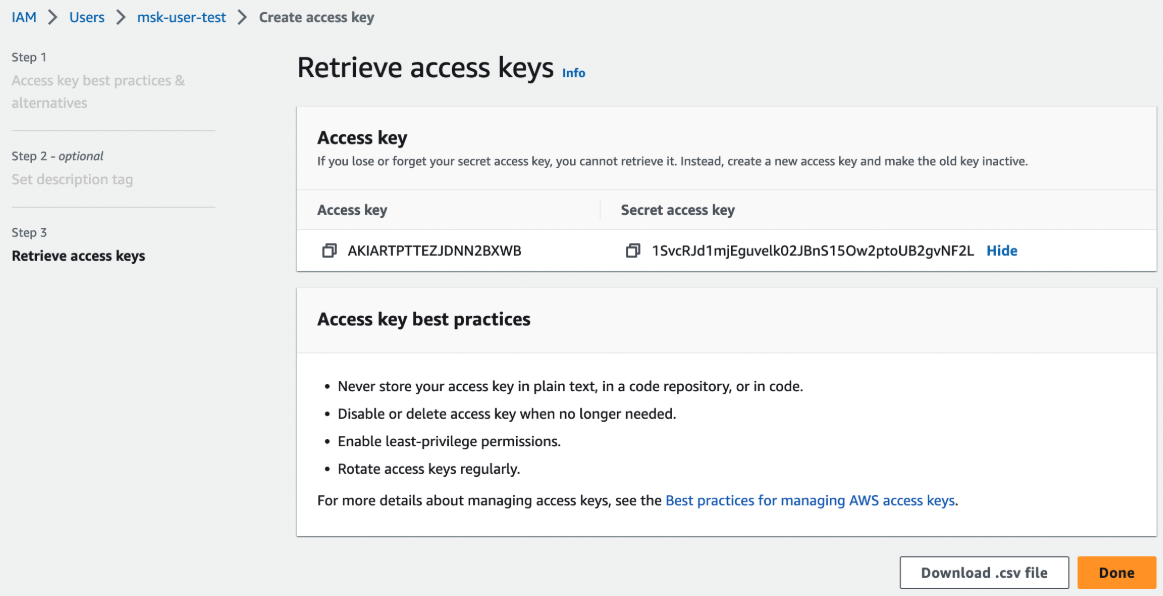
- Generate an access key:
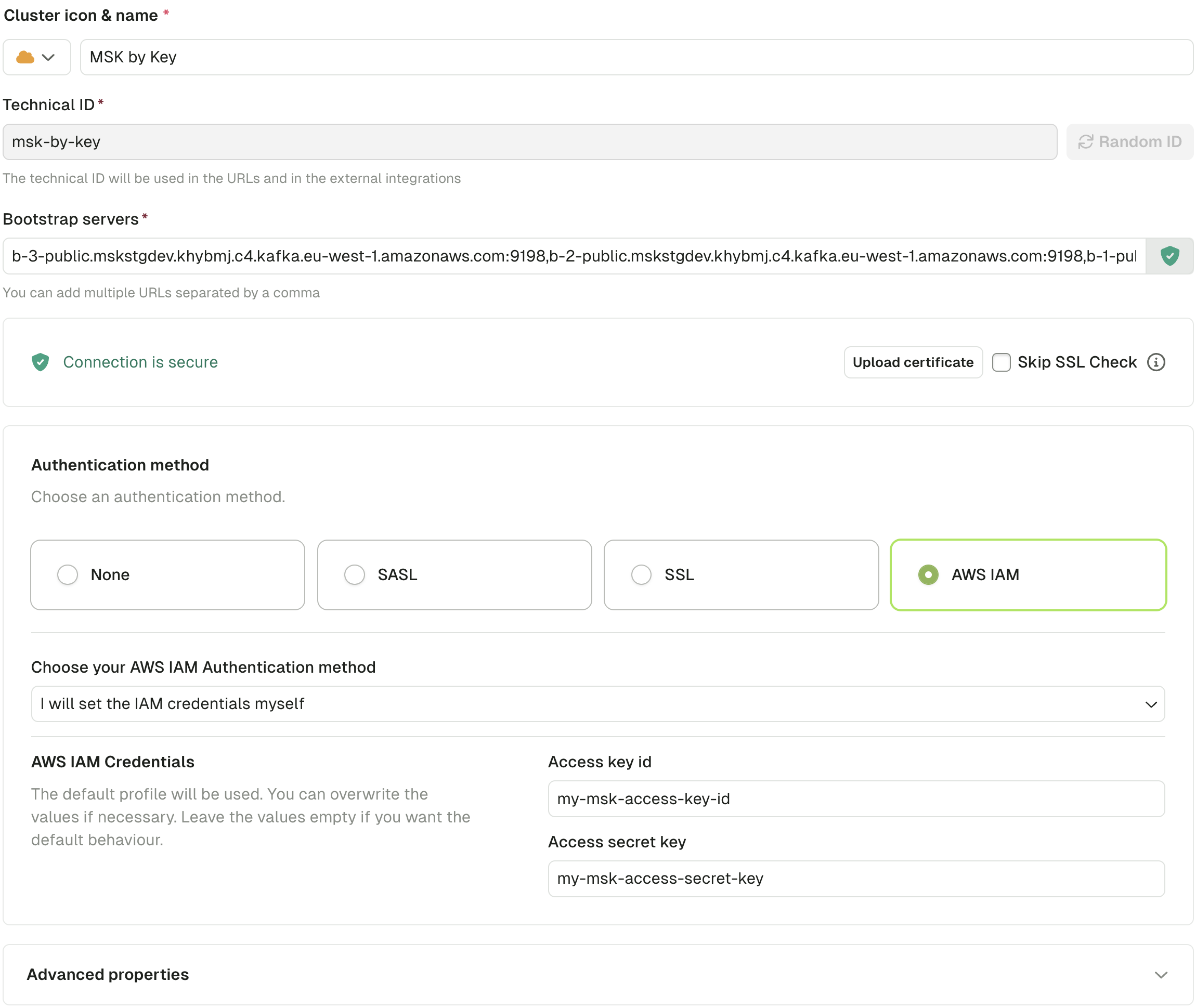
- In Console, enter the Bootstrap server and select AWS IAM as the authentication method
- Choose one option:
- Inherit credentials from environment variables, or
- Enter the Access Key and Secret Key
Connect to a Cloudera cluster
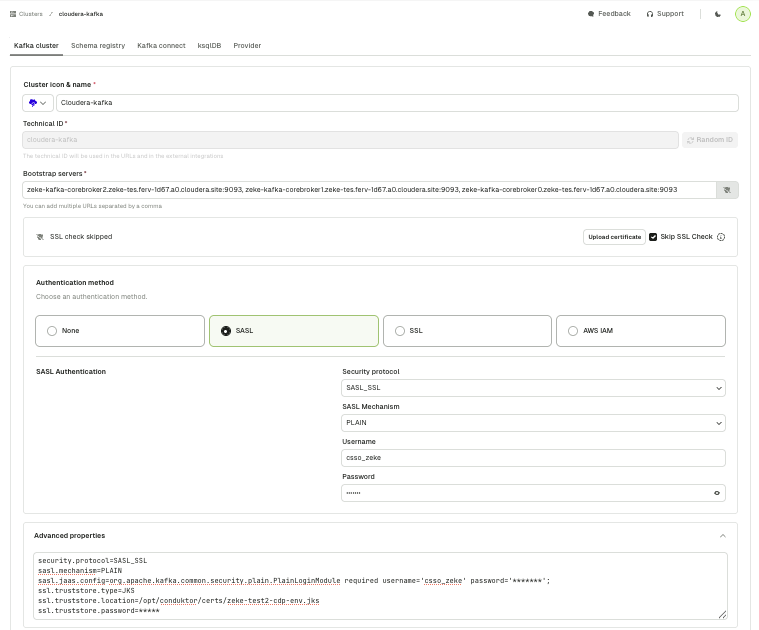
These instructions use SASL_SSL protocol with PLAIN mechanism.
- Create a workload user with ownership of the Data Hub cluster. Note the username and password:
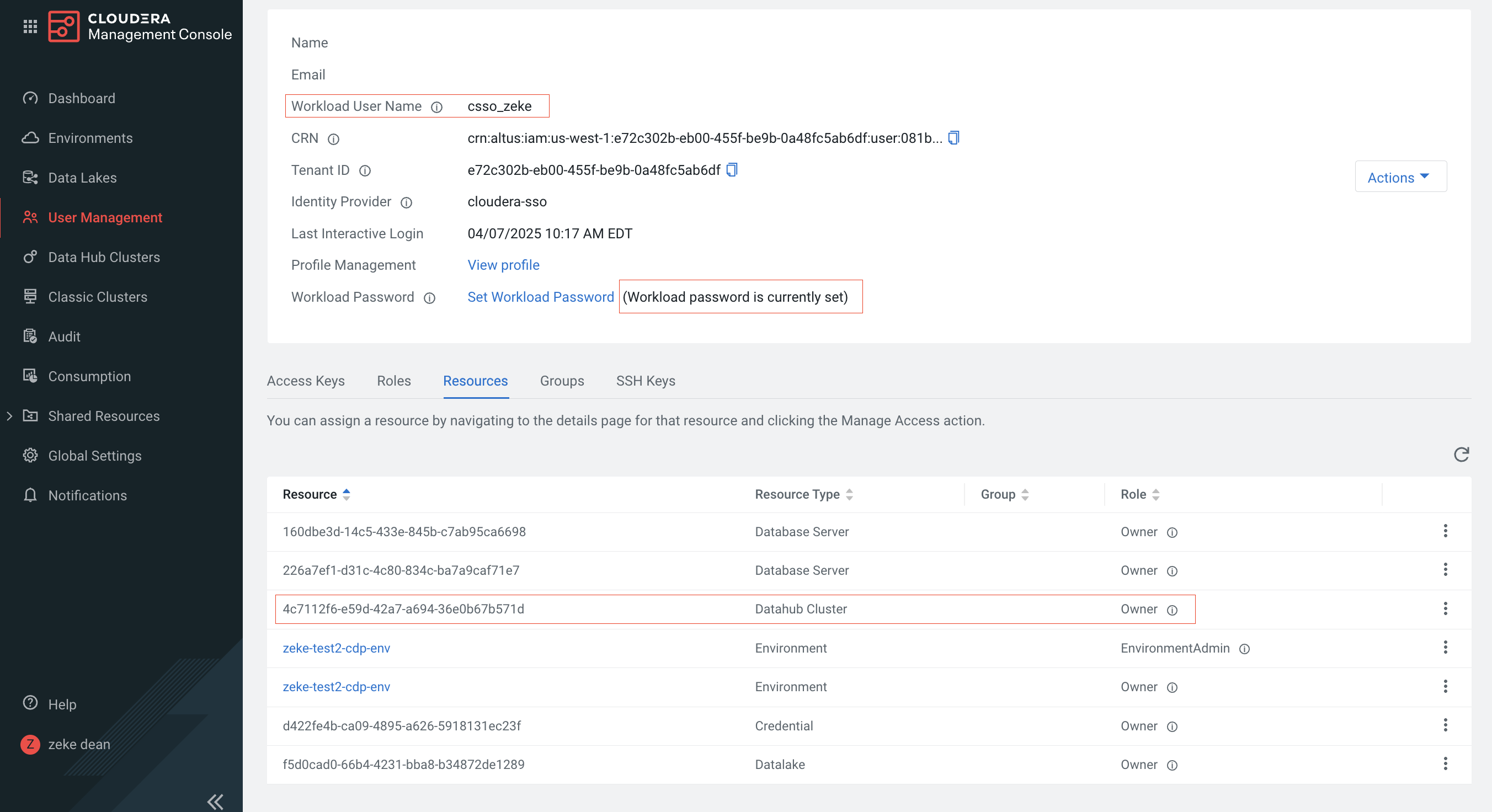
- Download certificates from Cloudera:
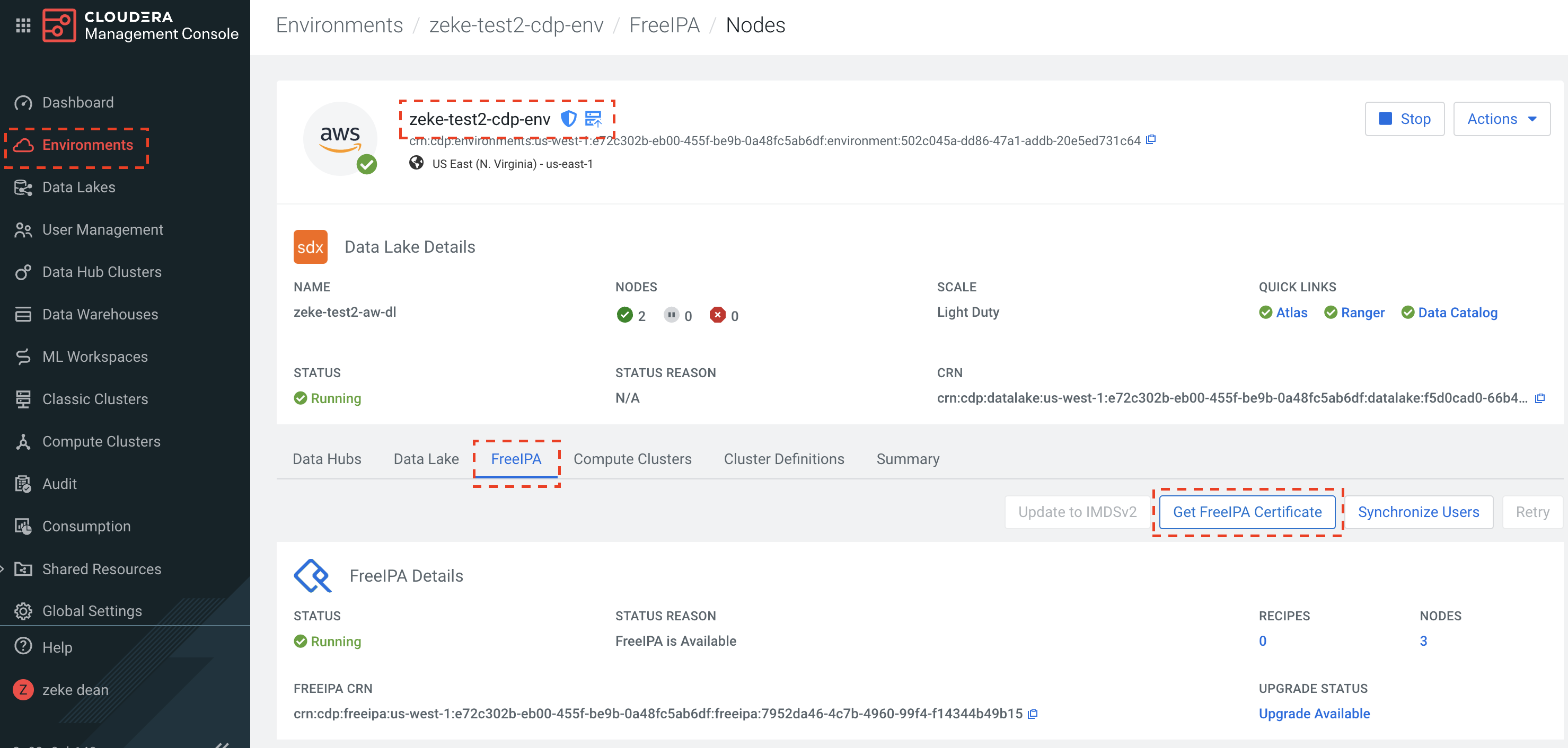
- Convert CRT certificates to JKS format using Java keytool:
- In Cloudera, open firewalls for Kafka brokers and Schema Registry
- In Console, go to Clusters, select the Cloudera cluster, and upload the certificates
- Configure the cluster using the workload username and password from step 1:
Connect to a Google Cloud cluster
Connect to Google Cloud Managed Service for Apache Kafka using SASL_SSL protocol with PLAIN mechanism.Use a service account
View Google Cloud documentationUse an access token
- Get an access token:
- Use the token with these parameters:
- The access token is valid and not expired
- The username matches the principal email associated with the access token
- The principal has the
managedkafka.clusters.connectpermission (included inroles/managedkafka.client)