Console resources
ConsoleGroup
API Keys: Admin API Key Managed with: API CLI Terraform Console UI Labels support: Label Support Incoming
Creates a Group with members and permissions in Console
- CLI
- Terraform
---
apiVersion: iam/v2
kind: Group
metadata:
name: developers-a
spec:
displayName: "Developers Team A"
description: "Members of the Team A - Developers"
externalGroups:
- "LDAP-GRP-A-DEV"
members:
- member1@company.org
- member2@company.org
permissions:
- resourceType: TOPIC
cluster: shadow-it
patternType: PREFIXED
name: toto-
permissions:
- topicViewConfig
- topicConsume
- topicProduce
resource "conduktor_console_group_v2" "developers-a" {
name = "developers-a"
spec = {
display_name = "Developers Team A"
description = "Members of the Team A - Developers"
external_groups = [ "LDAP-GRP-A-DEV" ]
members = [ "member1@company.org", "member1@company.org" ]
permissions = [
{
resource_type = "TOPIC"
cluster = "shadow-it"
pattern_type = "PREFIXED"
name = "toto-"
permissions = ["topicViewConfig", "topicConsume", "topicProduce"]
}
]
}
}
Groups checks:
spec.descriptionis optionalspec.externalGroupsis a list of LDAP or OIDC groups to sync with this Console Group- Members added this way will not appear in
spec.membersbutspec.membersFromExternalGroupsinstead
- Members added this way will not appear in
spec.membersFromExternalGroupsis a read-only list of members added throughspec.externalGroupsspec.membersmust be email addresses of members you wish to add to this groupspec.permissionsare valid permissions as defined in Permissions
Side effect in Console & Kafka:
- Console
- Members of the Group are given the associated permissions in the UI over the resources
- Members of the LDAP or OIDC groups will be automatically added or removed upon login
- Kafka
- No side effect
ConsoleUser
API Keys: Admin API Key Managed with: API CLI Terraform Console UI Labels support: Label Support Incoming
Create a user with Platform permissions.
- CLI
- Terraform
---
apiVersion: iam/v2
kind: User
metadata:
name: john.doe@company.org
spec:
firstName: "John"
lastName: "Doe"
permissions:
- resourceType: PLATFORM
permissions:
- taasView
- datamaskingView
- resourceType: TOPIC
cluster: shadow-it
patternType: PREFIXED
name: toto-
permissions:
- topicViewConfig
- topicConsume
- topicProduce
resource "conduktor_console_user_v2" "john.doe@company.org" {
name = "john.doe@company.org"
spec = {
firstname = "John"
lastname = "Doe"
permissions = [
{
resource_type = "TOPIC"
cluster = "shadow-it"
patternType = "PREFIXED"
name = "toto-"
permissions = [
"topicViewConfig",
"datamaskingView",
"auditLogView"
]
},
{
resource_type = "PLATFORM"
permissions = [
"taasView",
"datamaskingView"
]
}
]
}
}
Make sure you set permissions for this user, otherwise it won't have access to Platform functionality (such as Application Catalog or Data Policies) and Kafka resources.
Users checks:
spec.permissionsare valid permissions as defined in Permissions
Side effect in Console & Kafka:
- Console
- User is given the associated permissions in the UI over the resources
- Kafka
- No side effect
KafkaCluster
Creates a Kafka Cluster Definition in Console.
API Keys: Admin API Key Managed with: API CLI Terraform Console UI Labels support: Partial Label Support (No UI yet)
- CLI
- Terraform
---
apiVersion: console/v2
kind: KafkaCluster
metadata:
name: my-dev-cluster
spec:
displayName: "My Dev Cluster"
icon: "kafka"
color: "#000000"
bootstrapServers: "localhost:9092"
ignoreUntrustedCertificate: false
properties:
sasl.jaas.config: org.apache.kafka.common.security.plain.PlainLoginModule required username="admin" password="admin-secret";
security.protocol: SASL_SSL
sasl.mechanism: PLAIN
schemaRegistry:
type: "ConfluentLike"
url: http://localhost:8080
security:
type: BasicAuth
username: some_user
password: some_password
ignoreUntrustedCertificate: false
kafkaFlavor:
type: "Confluent"
key: "string"
secret: "string"
confluentEnvironmentId: "string"
confluentClusterId: "string"
resource "conduktor_console_kafka_cluster_v2" "my-dev-cluster" {
name = "my-dev-cluster"
spec = {
display_name = "My Dev Cluster"
icon = "kafka"
color = "#000000"
bootstrap_servers = "localhost:9092"
ignore_untrusted_certificate = false
properties = {
"sasl.jaas.config" = "org.apache.kafka.common.security.plain.PlainLoginModule required username='admin' password='admin-secret';"
"security.protocol" = "SASL_SSL"
"sasl.mechanism" = "PLAIN"
}
schema_registry = {
type = "ConfluentLike"
url = "http://localhost:8080"
security = {
type = "BasicAuth"
username = "some_user"
password = "some_password"
}
ignore_untrusted_certificate = false
}
kafka_flavor = {
type = "Confluent"
key = "string"
secret = "string"
confluent_environment_id = "string"
confluent_cluster_id = "string"
}
}
}
metadata.name, spec.displayName, spec.icon and spec.color work together to build the visual identity of the KafkaCluster throughout Console.
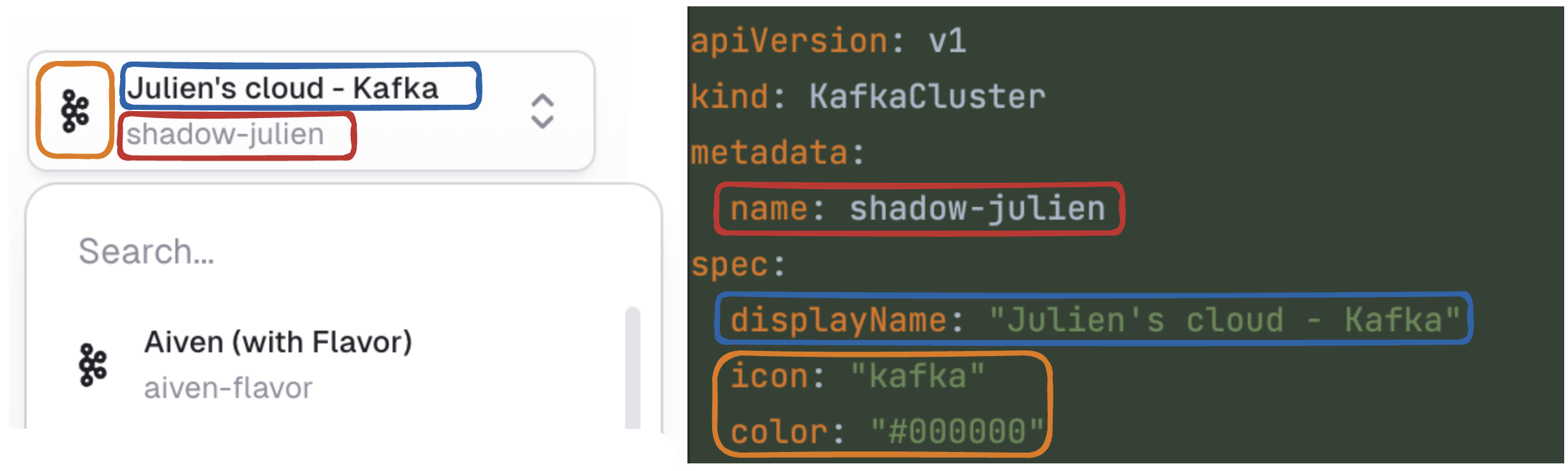
KafkaCluster checks:
spec.icon(optional, defaultkafka) is a valid entry from our Icon Setsspec.color(optional, default#000000) is a HEX color forspec.iconspec.ignoreUntrustedCertificate(optional, defaultfalse) must be one of [true,false]spec.schemaRegistry.type(optional) must be one of [ConfluentLike,Glue]- See Schema Registry Properties for the detailed list of options
spec.kafkaFlavor.type(optional) must be one of [Confluent,Aiven,Gateway]- See Kafka Provider Properties for the detailed list of options
Conduktor CLI does not verify that your Kafka configuration (spec.bootstrapServers, spec.properties, ...) is valid.
You need to check that in Console directly.
Schema Registry
This section lets you associate a Schema Registry to your KafkaCluster
Confluent or Confluent-like Registry
- CLI
- Terraform
spec:
schemaRegistry:
type: "ConfluentLike"
url: http://localhost:8080
ignoreUntrustedCertificate: false
security:
type: BasicAuth
username: some_user
password: some_password
spec = {
schema_registry = {
type = "ConfluentLike"
url = "http://localhost:8080
ignore_untrusted_certificate = false
security = {
type = "BasicAuth"
username = "some_user"
password = "some_password"
}
}
}
Confluent Schema Registry checks:
spec.schemaRegistry.urlsmust be a single URL of a Kafka Connect cluster- Multiple URLs are not supported for now. Coming soon
spec.schemaRegistry.ignoreUntrustedCertificate(optional, defaultfalse) must be one of [true,false]spec.schemaRegistry.properties(optional) is Java Properties formatted key values to further configure the SchemaRegistryspec.security.type(optional) must be one of [BasicAuth,BearerToken,SSLAuth]- See HTTP Security Properties for the detailed list of options
AWS Glue Registry
- CLI
- Terraform
spec:
schemaRegistry:
type: "Glue"
region: eu-west-1
registryName: default
security:
type: Credentials
accessKeyId: accessKey
secretKey: secretKey
spec = {
schema_registry = {
type = "Glue"
region = "eu-west-1"
registry_name = "default"
security = {
type = "Credentials"
access_key_id = "accessKey"
secret_key = "secretKey"
}
}
}
AWS Glue Registry checks:
spec.schemaRegistry.regionmust be a valid AWS regionspec.schemaRegistry.registryNamemust be a valid AWS Glue Registry in this regionspec.schemaRegistry.security.typemust be one of [Credentials,FromContext,FromRole]
Credentials Use AWS API Key/Secret to connect to the Glue Registry
- CLI
- Terraform
security:
type: Credentials
accessKeyId: AKIAIOSFODNN7EXAMPLE
secretKey: wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY
security = {
type = "Credentials"
access_key_id = "AKIAIOSFODNN7EXAMPLE"
secret_key = "wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY"
}
FromContext
- CLI
- Terraform
security:
type: FromContext
profile: default
security = {
type = "FromContext"
profile = "default"
}
FromRole
- CLI
- Terraform
security:
type: FromRole
role: arn:aws:iam::123456789012:role/example-role
security = {
type = "FromRole"
profile = "arn:aws:iam::123456789012:role/example-role"
}
Kafka Provider
This section lets you configure the Kafka Provider for this KafkaCluster.
Confluent Cloud Provide your Confluent Cloud details to get additional features in Console:
- Confluent Cloud Service Accounts support
- Confluent Cloud API Keys support
- CLI
- Terraform
spec:
kafkaFlavor:
type: "Confluent"
key: "yourApiKey123456"
secret: "yourApiSecret123456"
confluentEnvironmentId: "env-12345"
confluentClusterId: "lkc-67890"
spec = {
kafka_flavor = {
type = "Confluent"
key = "yourApiKey123456"
secret = "yourApiSecret123456"
confluent_environment_id = "env-12345"
confluent_cluster_id = "lkc-67890"
}
}
Aiven Provide your Aiven Cloud details to get additional features in Console:
- Aiven Service Accounts support
- Aiven ACLs support
- CLI
- Terraform
spec:
kafkaFlavor:
type: "Aiven"
apiToken: "a1b2c3d4e5f6g7h8i9j0"
project: "my-kafka-project"
serviceName: "my-kafka-service"
spec = {
kafka_flavor = {
type = "Aiven"
api_token = "a1b2c3d4e5f6g7h8i9j0"
project = "my-kafka-project"
service_name = "my-kafka-service"
}
}
Gateway Provide your Gateway details to get additional features in Console:
- Interceptors support
- CLI
- Terraform
spec:
kafkaFlavor:
type: "Gateway"
url: "http://gateway:8888"
user: "admin"
password: "admin"
virtualCluster: passthrough
spec = {
kafka_flavor = {
type = "Gateway"
url = "http://gateway:8888"
user = "admin"
password = "admin"
virtual_cluster = "passthrough"
ignore_untrusted_certificate = false
}
}
Icon Sets
cloudBolt | cloudRainbow | cloud | snowflake |
pooStorm | poop | bolt | umbrella |
tennisBall | rugbyBall | trafficCone | faucet |
basketShopping | box | scaleBalanced | sunglasses |
sword | axeBattle | vial | featherPointed |
bomb | flag | heart | key |
fireExtinguisher | fireFlameCurved | alien | helmetBattle |
ghost | robot | dog | elephant |
bird | crab | catSpace | planetRinged |
meteor | moon | spaceStation | rocketLaunch |
paperPlane | carSide | buildingColumns | castle |
acorn | burgerLettuce | croissant | mug |
cactus | clover | cameraCctv | calendar |
alarmClock | compass | gamepadModern | server |
shieldBlank | computerClassic | dharmachakra | kafka |
KafkaConnectCluster
Creates a Kafka Connect Cluster Definition in Console.
API Keys: Admin API Key Managed with: API CLI Terraform Console UI Labels support: Partial Label Support (No UI yet)
- CLI
- Terraform
---
apiVersion: console/v2
kind: KafkaConnectCluster
metadata:
cluster: my-dev-cluster
name: connect-1
spec:
displayName: "Connect 1"
urls: "http://localhost:8083"
headers:
X-PROJECT-HEADER: value
AnotherHeader: test
ignoreUntrustedCertificate: false
security:
type: "BasicAuth"
username: "toto"
password: "my-secret"
resource "conduktor_console_kafka_connect_v2" "connect-1" {
name = "connect-1"
cluster = "my-dev-kafka-cluster"
spec = {
display_name = "Connect 1"
urls = "http://localhost:8083"
headers = {
X-PROJECT-HEADER = "value"
Cache-Control : "no-cache"
}
ignore_untrusted_certificate = false
security = {
type = "BasicAuth"
username = "toto"
password = "my-secret"
}
}
}
KafkaConnectCluster checks:
metadata.clustermust be a valid KafkaCluster namespec.urlsmust be a single URL of a Kafka Connect cluster- Multiple URLs are not supported for now. Coming soon
spec.ignoreUntrustedCertificate(optional, defaultfalse) must be one of [true,false]spec.headers(optional) must be key-value pairs of HTTP Headersspec.security.type(optional) must be one of [BasicAuth,BearerToken,SSLAuth]- See HTTP Security Properties for the detailed list of options
KsqlDBCluster
API Keys: Admin API Key Managed with: API CLI Console UI Labels support: Label Support Incoming
Creates a ksqlDB Cluster Definition in Console.
---
apiVersion: console/v2
kind: KsqlDBCluster
metadata:
cluster: my-dev-cluster
name: ksql-1
spec:
displayName: "KSQL 1"
url: "http://localhost:8088"
ignoreUntrustedCertificate: false
security:
type: "BasicAuth"
username: "toto"
password: "my-secret"
KafkaConnectCluster checks:
metadata.clustermust be a valid KafkaCluster namespec.urlmust be a single URL of a KsqlDB clusterspec.ignoreUntrustedCertificate(optional, defaultfalse) must be one of [true,false]spec.headers(optional) must be key-value pairs of HTTP Headersspec.security.type(optional) must be one of [BasicAuth,BearerToken,SSLAuth]- See HTTP Security Properties for the detailed list of options
Alert
API Keys: Admin API Key Application API Key Managed with: API CLI Console UI Labels support: Label Support Incoming
Creates an Alert in Console.
---
apiVersion: console/v3
kind: Alert
metadata:
name: messages-in-dead-letter-queue
group: support-team # will be the owner of the alert, can be either a user, a group or an appInstance
# user: user@company.org
# appInstance: my-app-instance
spec:
cluster: my-dev-cluster
type: TopicAlert
topicName: wikipedia-parsed-DLQ
metric: MessageCount
operator: GreaterThan
threshold: 0
destination:
type: Slack
channel: "alerts-p1"
Alert checks:
metadata.user|metadata.group|metadata.appInstancehas to be a valid user, group or appInstancemetadata.destination.typecan be eitherSlack,TeamsorWebhookspec.clusterhas to be a valid KafkaCluster namespec.typehas to be one of [BrokerAlert,TopicAlert,KafkaConnectAlert]- Check the section below for the additional mandatory fields needed for each
spec.type
- Check the section below for the additional mandatory fields needed for each
spec.metricis depending on thespec.type- Check section below
spec.operatorhas to be one of [GreaterThan,GreaterThanOrEqual,LessThan,LessThanOrEqual,NotEqual]spec.thresholdhas to be a numberspec.disable(optional, defaultfalse) has to be one of [true,false]
When spec.destination.type is Slack
spec.destination.channelhas to be a valid Slack channel id
When spec.destination.type is Teams
spec.destination.urlhas to be a valid Teams webhook URL
When spec.destination.type is Webhook
spec.destination.urlhas to be a valid URLspec.destination.methodhas to be one of [GET,POST,PUT,DELETE]spec.destination.headers(optional) has to be key-value pairs of HTTP Headersspec.destination.authentification.type(optional) has to be one of [BasicAuth,BearerToken]- when is
BasicAuthspec.destination.authentification.usernameandspec.destination.authentification.passwordhas to be set - when is
BearerTokenspec.destination.authentification.tokenhas to be set
- when is
When spec.type is BrokerAlert
spec.metrichas to be one of [MessageIn,MessageOut,MessageSize,OfflinePartitionCount,PartitionCount,UnderMinIsrPartitionCount,UnderReplicatedPartitionCount]
When spec.type is TopicAlert
spec.metrichas to be one of [MessageCount,MessageIn,MessageOut,MessageSize]spec.topicNamehas to be a Kafka Topic that the owner can access
When spec.type is KafkaConnectAlert
spec.metrichas to beFailedTaskCountspec.connectNamehas to be a valid KafkaConnect Cluster associated to thisspec.clusterKafka Clusterspec.connectorNamehas to be a Kafka Connect Connector that the owner can access
When spec.type is ConsumerGroupAlert
spec.metrichas to be one of [OffsetLag,TimeLag]spec.consumerGroupNamehas to be a Kafka Consumer Group that the owner can access
DataMaskingPolicy
This concept will be available in a future version
Partner Zone
API Keys: Admin API Key Managed with: API CLI Console UI Labels support: Partial Label Support (No UI yet)
Create or update a Partner Zone.
---
apiVersion: console/v2
kind: PartnerZone
metadata:
name: external-partner-zone
spec:
displayName: External Partner Zone
description: An external partner to exchange data with.
url: https://partner1.com
partner:
name: John Doe
role: Data analyst
email: johndoe@partner.io
phone: 07827 837 177
cluster: cdk-gateway
authenticationMode:
serviceAccount: partner-external-partner
type: PLAIN
topics:
- name: topic-a
backingTopic: kafka-topic-a
permission: WRITE
- name: topic-b
backingTopic: kafka-topic-a
permission: READ
trafficControlPolicies:
maxProduceRate: 1e+06
maxConsumeRate: 1e+06
limitCommitOffset: 30
headers:
addOnProduce:
- key: partner-name
value: external-analytics-partner
overrideIfExists: false
- key: client-info
value: "Client:{{clientId}}, from IP:{{userIp}}"
overrideIfExists: true
- key: kafka-api
value: "Kafka API Key:{{apiKey}}, version {{apiKeyVersion}}"
overrideIfExists: true
- key: produce-metadata
value: "User:{{user}}, via Gateay:{{gatewayHost}}, at timestampMillis:{{timestampMillis}}"
overrideIfExists: true
removeOnConsume:
- keyRegex: my_team_prefix.*
Partner Zone checks:
-
spec.displayNameis mandatory -
spec.description,spec.urlandspec.partnerare optional context informations. -
spec.clusterhas to be a valid Console cluster technical ID with the Provider set asGateway. -
spec.authenticationMode.typehas to be one of [PLAIN,OAUTHBEARER,MTLS]- When
spec.authenticationMode.typeisPLAINspec.authenticationMode.serviceAccountwill be created automatically, it doesn't need to exist before creating the Partner Zone. This is a local Gateway service account.
- When
spec.authenticationMode.typeisOAUTHBEARERspec.authenticationMode.serviceAccountwill be created automatically and needs to match the "sub" (subject) claim present in the OAuth token. This is an external Gateway service account.
- When
spec.authenticationMode.typeisMTLSspec.authenticationMode.serviceAccountwill be created automatically, it doesn't need to exist before creating the Partner Zone. This is an external Gateway service account.- You still need to create the certificate and share it with the partner. The certificate has to have the
CNmatch the name of this service account.
- When
-
topics[].nameis the name of the topic as it should appear to your partner. This can be different frombackingTopic. -
topics[].backingTopicis the internal name of the topic that you want to share with your partner. -
topics[].permissionhas to be set to eitherREADorWRITE(which additionally grantsREAD). -
trafficControlPolicies.maxProduceRateis optional. Sets the maximum rate (in bytes/s) at which the partner can produce messages to the topics per Gateway node. -
trafficControlPolicies.maxConsumeRateis optional. Sets the maximum rate (in bytes/s) at which the partner can consume messages from the topics per Gateway node. -
trafficControlPolicies.limitCommitOffsetis optional. Sets the maximum number of commits requests (in requests/minute) that the partner can make per Gateway node. -
headers.addOnProduce.keyis optional. Sets the key of a key:value pair to be added when producing to the partner zone i.e. from the partner producing messages. -
headers.addOnProduce.valueis optional. Sets the value of a key:value pair to be added when producing to the partner zone i.e. from the partner producing messages. -
headers.addOnProduce.overrideIfExistsis optional. Determines what to do if this header already exists. -
headers.RemoveOnConsume.keyRegexis optional. Regular expression for finding the keys of headers to be removed on consume of the partner zone, i.e. when the partner is reading messages.
Side effect in Console & Kafka: Upon creation or update, the following fields will be available:
metadata.updatedAtfield will be made available by consecutive get from the CLI/API.metadata.statusfield will be made available by consecutive get from the CLI/API. Possible values arePENDING,READYorFAILED.metadata.failedReasonfield will be populated in case ofFAILEDstatus.- The service account will be created if it doesn't exist and will be granted the permissions as declared in
spec.topics - The traffic control policies will be applied to the service account.
HTTP Security Properties
HTTP Security Properties are used in KafkaCluster (Schema Registry), KafkaConnect, KsqlDBCluster
Basic Authentication
security:
type: "BasicAuth"
username: "toto"
password: "my-secret"
Bearer Token
security:
type: "BearerToken"
token: "toto"
mTLS / Client certificate
security:
type: "SSLAuth"
key: |
-----BEGIN PRIVATE KEY-----
MIIOXzCCDUegAwIBAgIRAPRytMVYJNUgCbhnA+eYumgwDQYJKoZIhvcNAQELBQAw
...
IFyCs+xkcgvHFtBjjel4pnIET0agtbGJbGDEQBNxX+i4MDA=
-----END PRIVATE KEY-----
certificateChain: |
-----BEGIN CERTIFICATE-----
MIIOXzCCDUegAwIBAgIRAPRytMVYJNUgCbhnA+eYumgwDQYJKoZIhvcNAQELBQAw
RjELMAkGA1UEBhMCVVMxIjAgBgNVBAoTGUdvb2dsZSBUcnVzdCBTZXJ2aWNlcyBM
...
8/s+YDKveNdoeQoAmGQpUmxhvJ9rbNYj+4jiaujkfxT/6WtFN8N95r+k3W/1K4hs
IFyCs+xkcgvHFtBjjel4pnIET0agtbGJbGDEQBNxX+i4MDA=
-----END CERTIFICATE-----
Permissions
Permissions are used in Groups and Users and lets you configure all the access to any Kafka resource or Console feature.
A permission applies to a certain resourceType, which affect the necessary fields as detailed below.
- Topic Permissions
- Subject Permissions
- ConsumerGroup Permissions
- Cluster Permissions
- KafkaConnect Permissions
- KsqlDB Permissions
- Platform Permissions
Topic Permissions
# Grants Consume, Produce and View Config to all topics toto-* on shadow-it cluster
- resourceType: TOPIC
cluster: shadow-it
patternType: PREFIXED
name: toto-
permissions:
- topicViewConfig
- topicConsume
- topicProduce
resourceType:TOPICclusteris a valid Kafka clusterpatternTypeis eitherPREFIXEDorLITERALnameis the name of the topic or topic prefix to apply the permissions topermissionsis a list of valid topic permissions (See Table)
| Available Topic Permissions | Description |
|---|---|
topicConsume | Permission to consume messages from the topic. |
topicProduce | Permission to produce (write) messages to the topic. |
topicViewConfig | Permission to view the topic configuration. |
topicEditConfig | Permission to edit the topic configuration. |
topicCreate | Permission to create a new topic. |
topicDelete | Permission to delete the topic. |
topicAddPartition | Permission to add partitions to the topic. |
topicEmpty | Permission to empty (delete all messages from) the topic. |
Subject Permissions
# Grants View and Edit Compatibility to all subjects starting with sub-* on shadow-it cluster
- resourceType: SUBJECT
cluster: shadow-it
patternType: PREFIXED
name: sub-
permissions:
- subjectView
- subjectEditCompatibility
resourceType:SUBJECTclusteris a valid Kafka clusterpatternTypeis eitherPREFIXEDorLITERALnameis the name of the subject or subject prefix to apply the permissions topermissionsis a list of valid subject permissions (See Table)
| Available Subject Permissions | Description |
|---|---|
subjectCreateUpdate | Permission to create or update the subject. |
subjectDelete | Permission to delete the subject. |
subjectEditCompatibility | Permission to edit the subject compatibility settings. |
subjectView | Permission to view the subject details. |
ConsumerGroup Permissions
# Grants View and Reset on all consumer groups starting with group-* on shadow-it cluster
- resourceType: CONSUMER_GROUP
cluster: shadow-it
patternType: PREFIXED
name: group-
permissions:
- consumerGroupView
- consumerGroupReset
resourceType:CONSUMER_GROUPclusteris a valid Kafka clusterpatternTypeis eitherPREFIXEDorLITERALnameis the name of the consumer group or consumer group prefix to apply the permissions topermissionsis a list of valid consumer group permissions (See Table)
| Available ConsumerGroup Permissions | Description |
|---|---|
consumerGroupCreate | Permission to create a new consumer group. |
consumerGroupReset | Permission to reset the consumer group. |
consumerGroupDelete | Permission to delete the consumer group. |
consumerGroupView | Permission to view the consumer group details. |
Cluster Permissions
# Grants View Broker, Edit Schema Registry Compatibility, Edit Broker, View ACL, and Manage ACL on shadow-it cluster
- resourceType: CLUSTER
name: shadow-it
permissions:
- clusterViewBroker
- clusterEditSRCompatibility
- clusterEditBroker
- clusterViewACL
- clusterManageACL
resourceType:CLUSTERnameis the name of the cluster to apply the permissions to- Use
*for all clusters
- Use
permissionsis a list of valid cluster permissions (See Table)
| Available Cluster Permissions | Description |
|---|---|
clusterViewBroker | Permission to view broker details. |
clusterEditSRCompatibility | Permission to edit Schema Registry compatibility settings. |
clusterEditBroker | Permission to edit broker configuration. |
clusterViewACL | Permission to view Access Control Lists (ACLs) for the cluster. |
clusterManageACL | Permission to manage Access Control Lists (ACLs) for the cluster. |
KafkaConnect Permissions
# Grants Create and Delete on all connectors starting with connector-* on shadow-it cluster and kafka-connect-cluster
- resourceType: KAFKA_CONNECT
cluster: shadow-it
kafkaConnect: kafka-connect-cluster
patternType: PREFIXED
name: connector-
permissions:
- kafkaConnectorCreate
- kafkaConnectorDelete
resourceType:KAFKA_CONNECTclusteris a valid Kafka clusterkafkaConnectis a valid Kafka Connect clusterpatternTypeis eitherPREFIXEDorLITERALnameis the name of the connector or connector prefix to apply the permissions topermissionsis a list of valid Kafka Connect permissions (See Table)
| Available KafkaConnect Permissions | Description |
|---|---|
kafkaConnectorViewConfig | Permission to view the Kafka Connect configuration. |
kafkaConnectorStatus | Permission to view the status of Kafka Connect connectors. |
kafkaConnectorEditConfig | Permission to edit the Kafka Connect configuration. |
kafkaConnectorDelete | Permission to delete connectors. |
kafkaConnectorCreate | Permission to create new connectors. |
kafkaConnectPauseResume | Permission to pause and resume connectors. |
kafkaConnectRestart | Permission to restart connectors. |
KsqlDB Permissions
# Grants all permissions on KsqlDB cluster ksql-cluster
- resourceType: KSQLDB
cluster: shadow-it
ksqlDB: ksql-cluster
permissions:
- ksqldbAccess
resourceType:KSQLDBclusteris a valid Kafka clusterksqlDBis a valid Kafka Connect clusterpermissionsis a list of valid KsqlDB permissions (See Table)
| Available KafkaConnect Permissions | Description |
|---|---|
ksqldbAccess | Grants all permissions on the KsqlDB Cluster. |
Platform Permissions
# Grants Platform permissions
- resourceType: PLATFORM
permissions:
- userView
- datamaskingView
resourceType:PLATFORMpermissionsis a list of valid Platform permissions
| Available Platform permissions | Description |
|---|---|
clusterConnectionsManage | Permission to add / edit / remove Kafka clusters on Console |
certificateManage | Permission to add / edit / remove TLS Certificates on Console |
userManage | Permission to manage Console users, groups & permissions |
userView | Permission to view Console users, groups & permissions |
datamaskingManage | Permission to manage Data policies (masking rules) |
datamaskingView | Permission to view Data policies |
notificationChannelManage | Permission to manage Integration channels |
auditLogView | Permission to browse audit log |
taasView | Permission to view Application Catalog |
chargebackManage | Permission to view Chargeback and manage its settings |
sqlManage | Permission to view indexed topics and create SQL queries |