Configure Okta as SSO
Okta Configuration
On Okta side, you'll have to create a new application:
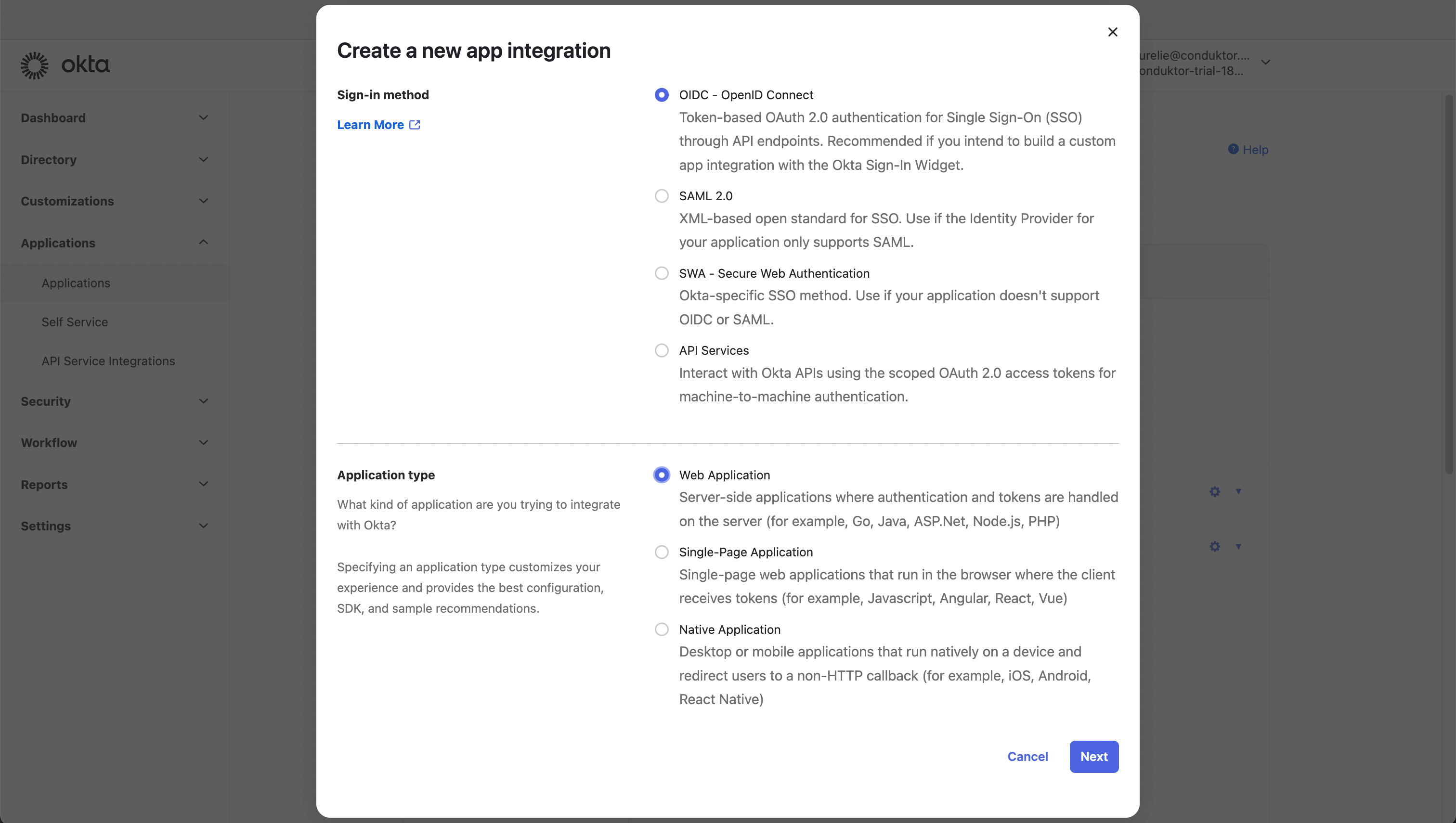
- Step 1: Create an OpenID Connect web application
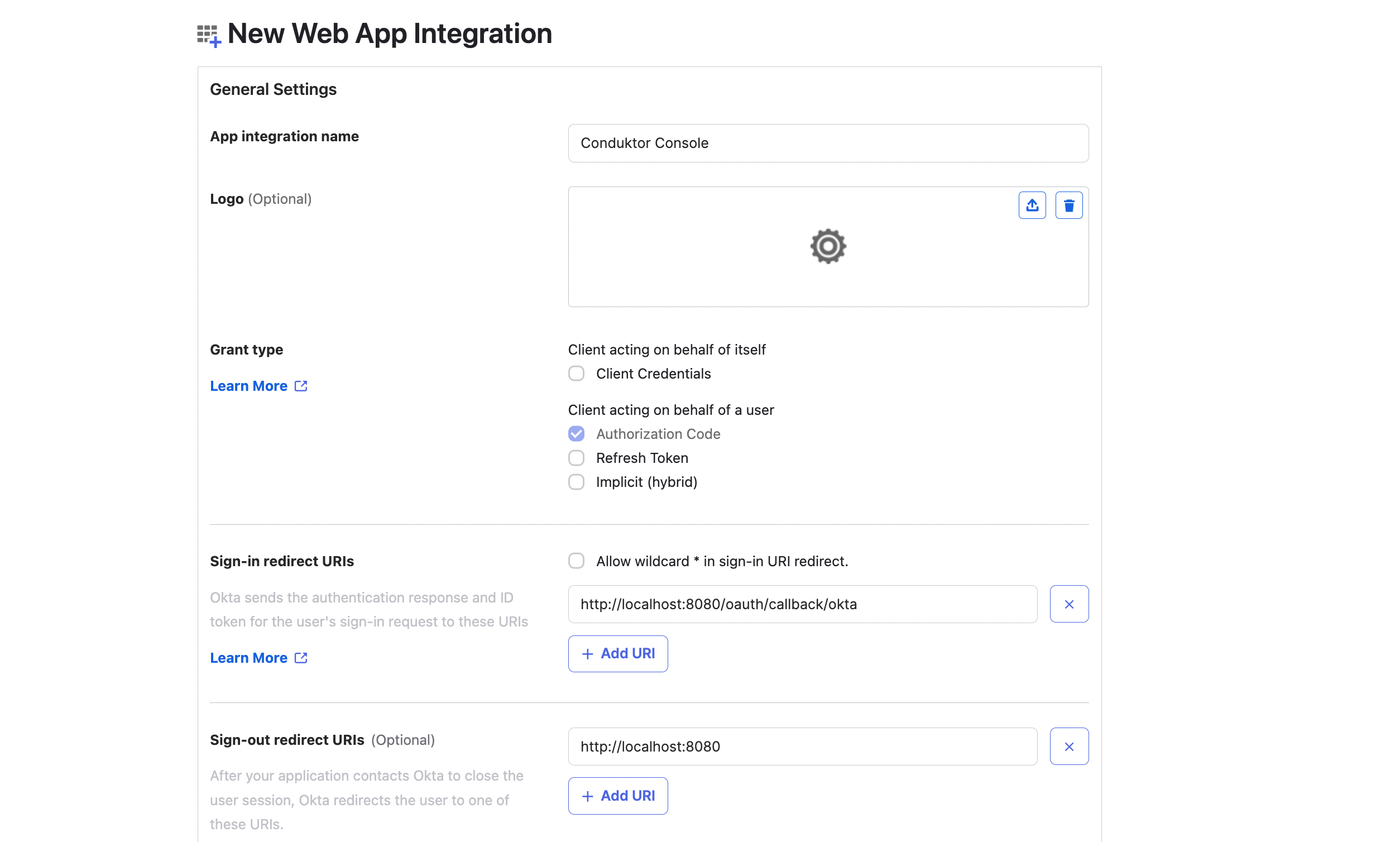
- Step 2: Configure the callback URI
The redirect URI can be like: http(s)://<Console host>(:<Console port>)/oauth/callback/<OAuth2 config name>.
For example, if you deployed Console locally using the name okta in your configuration file, you can use http://localhost:8080/oauth/callback/okta, like in the screenshot below.
For more details on Console redirect URI for OAuth2, you can check the documentation.
- Step 3: Configure app assignments, and save changes

- Step 4: Get
client IDandclient secret, that you'll use in the configuration file of Console

- Step 5: Find the
issuer URLin the Sign On tab of your application. It's made likehttps://<domain>.okta.com

You can find the .well-known at: https://<domain>.okta.com/.well-known/openid-configuration.
Console Configuration
On Console side, you can add the snippet below to your configuration file. You have to replace the client ID, client secret, and domain, with what you got during steps 4 and 5.
- YAML File
- Environment Variables
sso:
oauth2:
- name: "okta"
client-id: "<client ID>"
client-secret: "<client secret>"
openid:
issuer: "https://<domain>.okta.com"
Please note that if you are using a custom auth server in Okta, the OPENID_ISSUER should be in the form https://<yourOktaDomain>/oauth2/<authorizationServerId>/ rather than https://<domain>.okta.com
You can find documentation on this here.
CDK_SSO_OAUTH2_0_NAME="okta"
CDK_SSO_OAUTH2_0_DEFAULT=true
CDK_SSO_OAUTH2_0_CLIENT-ID="<client ID>"
CDK_SSO_OAUTH2_0_CLIENT-SECRET="<client secret>"
CDK_SSO_OAUTH2_0_OPENID_ISSUER="https://<domain>.okta.com"