Configure Keycloak as SSO
Keycloak Configuration
On Keycloak side, you'll have to create a new application:
- Step 1: create a new OpenID Connect client, and set the
client ID
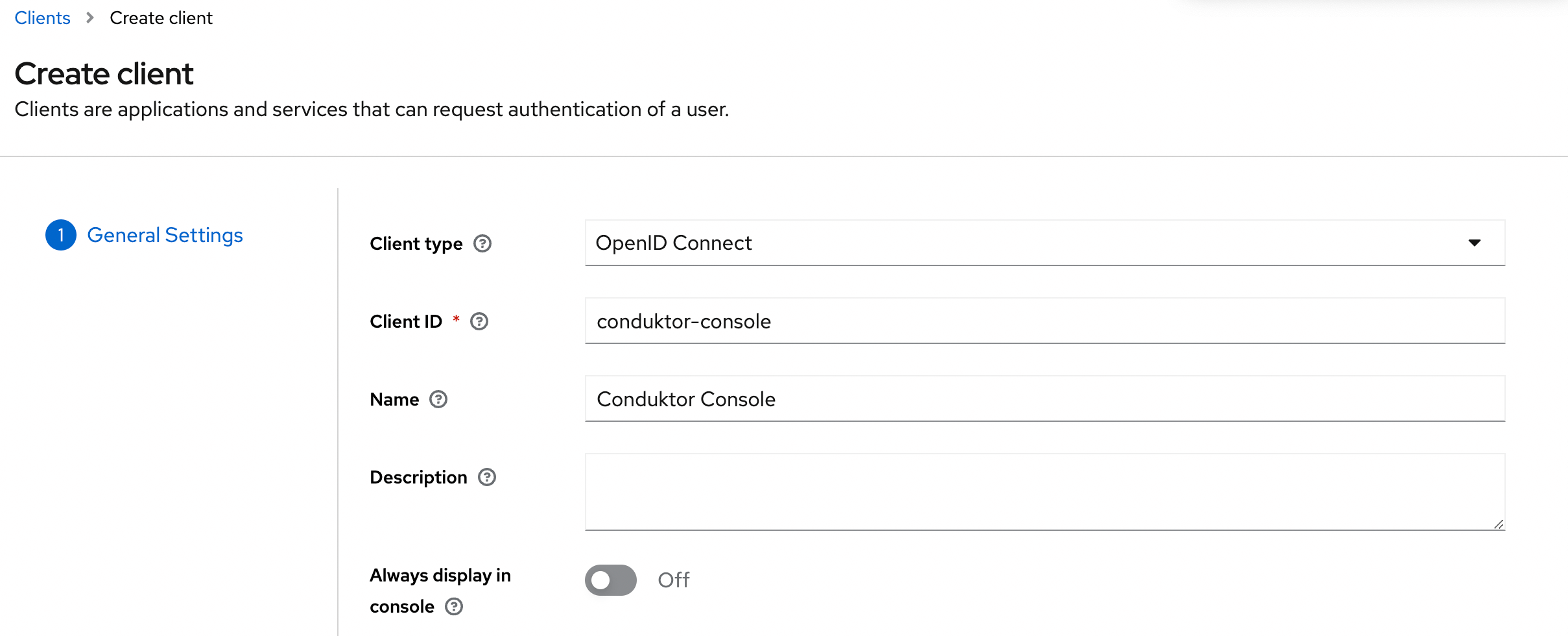
- Step 2: Select the Client authentication
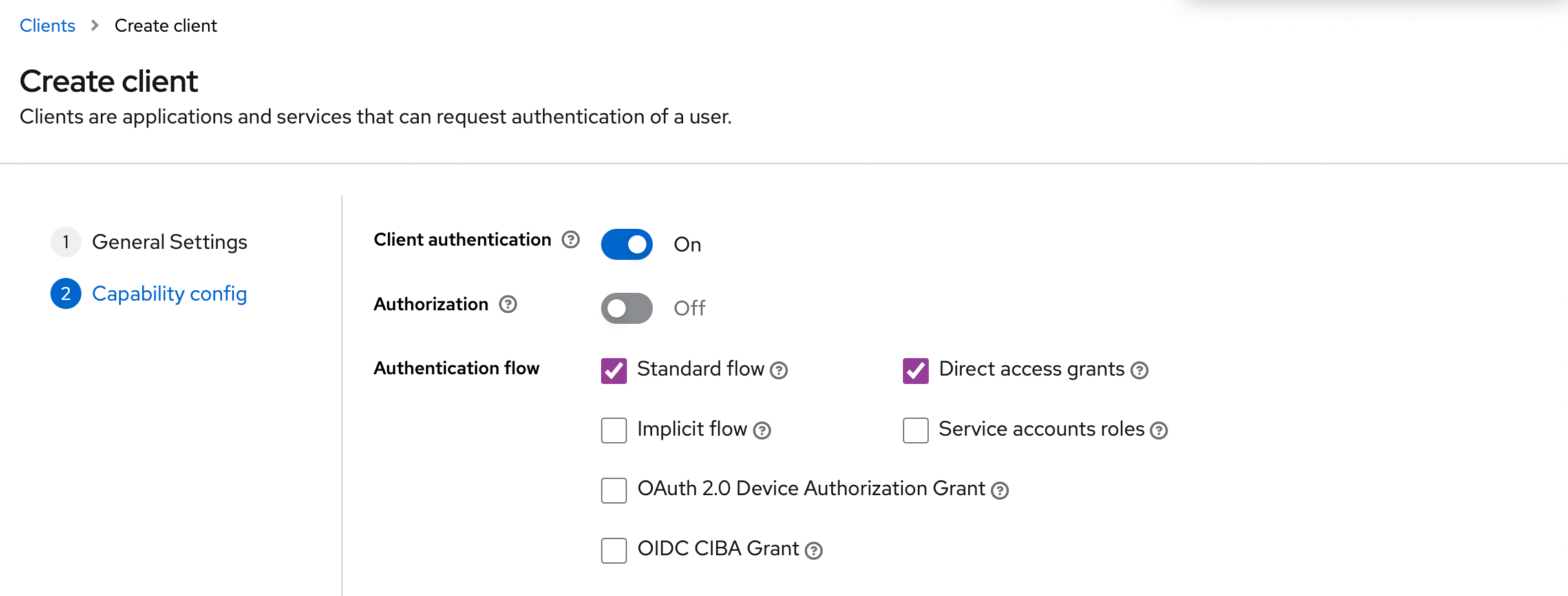
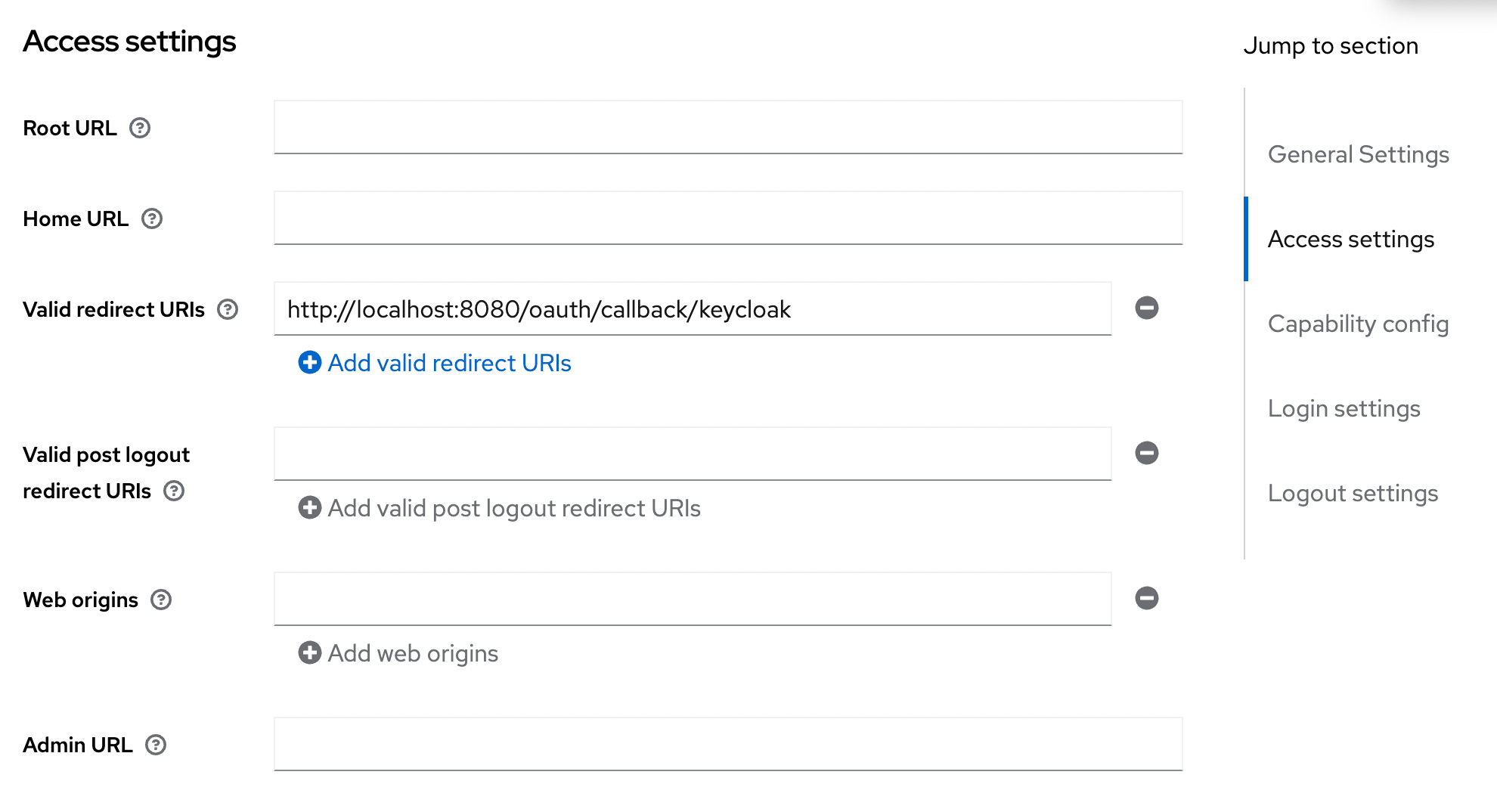
- Step 3: Configure the redirect URI
You can configure it as the following: http(s)://<Console host>(:<Console port>)/oauth/callback/<OAuth2 config name>
For example, if you deployed Console locally using the name keycloak in your configuration file, you can use http://localhost:8080/oauth/callback/keycloak, like in the screenshot below.
For more details on Console redirect URI for OAuth2, you can check the documentation.
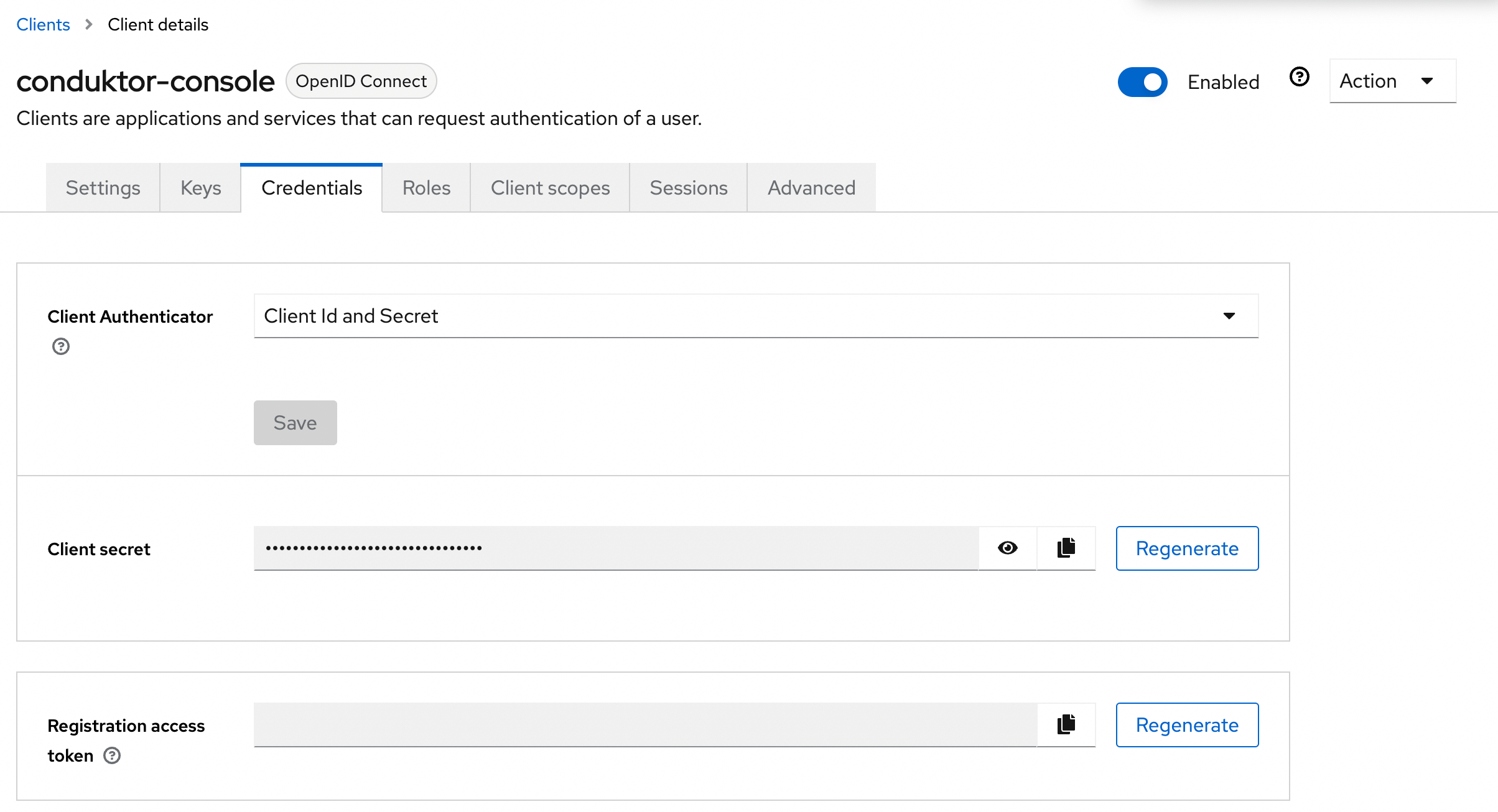
- Step 4: Get the
client secretin the Credentials tab
You can find the .well-known at: http://<Keycloak host>:<Keycloak port>/realms/<realm name>/.well-known/openid-configuration.
Console Configuration
On Console side, you can add the snippet below to your configuration file. You have to replace the client ID, client secret, and tenant ID, with what you got during the previous steps.
- YAML File
- Environment Variables
sso:
oauth2:
- name: "keycloak"
client-id: "<client ID>"
client-secret: "<client secret>"
openid:
issuer: "http://<Keycloak host>:<Keycloak port>/realms/<realm name>"
CDK_SSO_OAUTH2_0_NAME="keycloak"
CDK_SSO_OAUTH2_0_DEFAULT=true
CDK_SSO_OAUTH2_0_CLIENT-ID="<client ID>"
CDK_SSO_OAUTH2_0_CLIENT-SECRET="<client secret>"
CDK_SSO_OAUTH2_0_OPENID_ISSUER="http://<Keycloak host>:<Keycloak port>/realms/<realm name>"
Groups Configuration
If you want to use the external groups mapping to map groups between your Conduktor Console instance and Keycloak, you must create a scope and add it to your Keycloak application:
- Step 1: Create the scope and configure the mapper to Group Membership
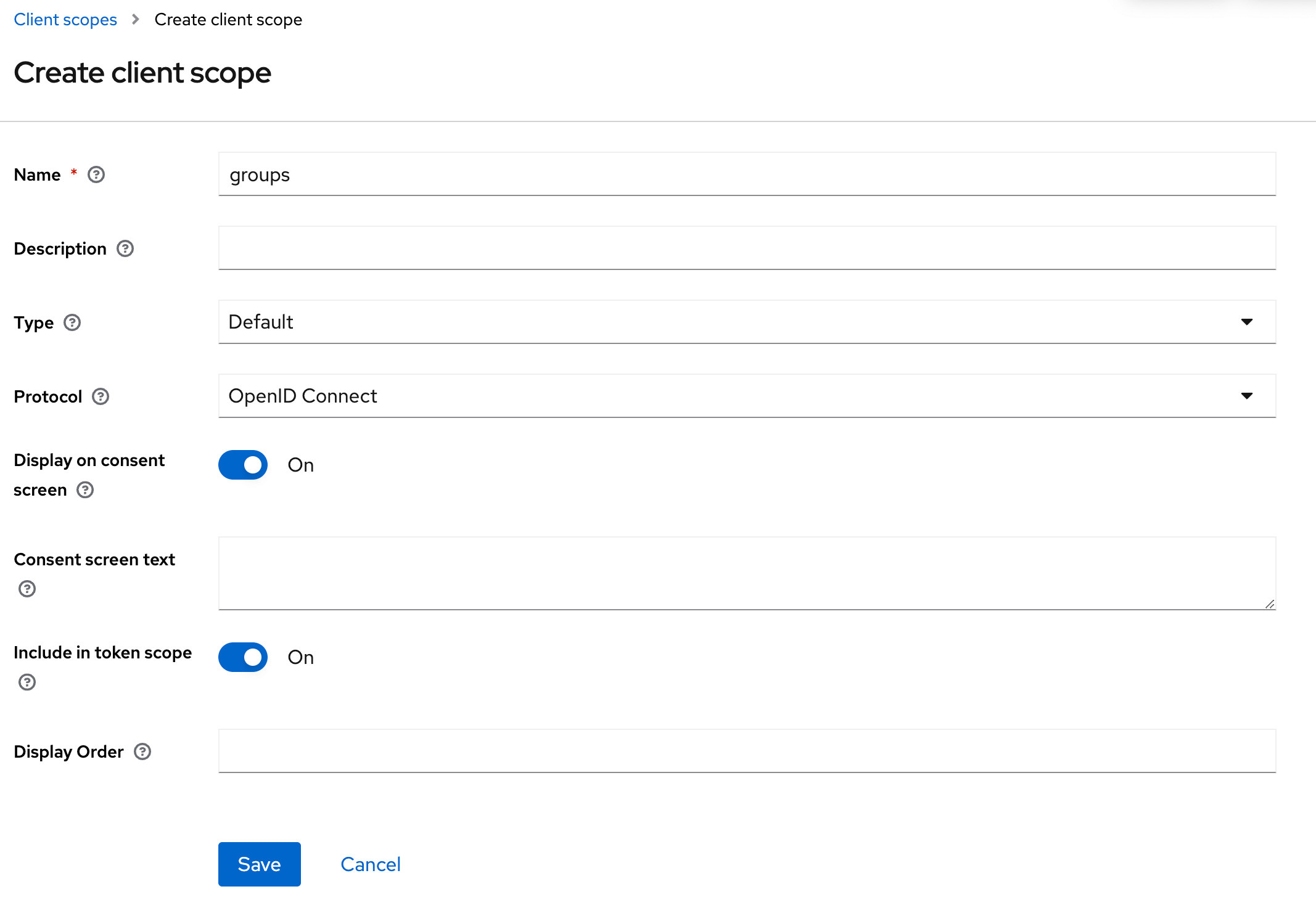
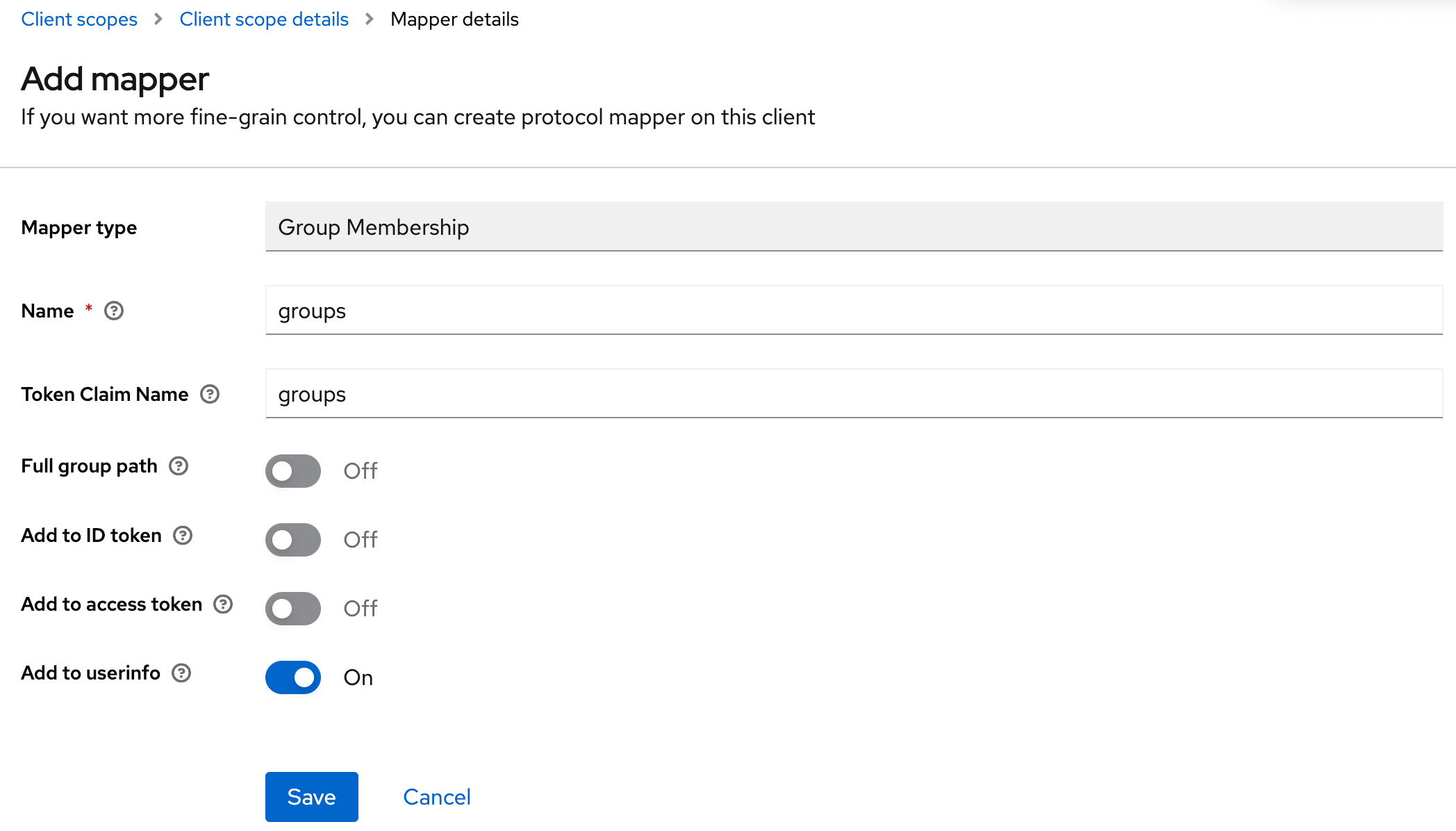
You can add the claim to the token you want. In this example, the UserInfo.
- Step 2: Add the scope to the application
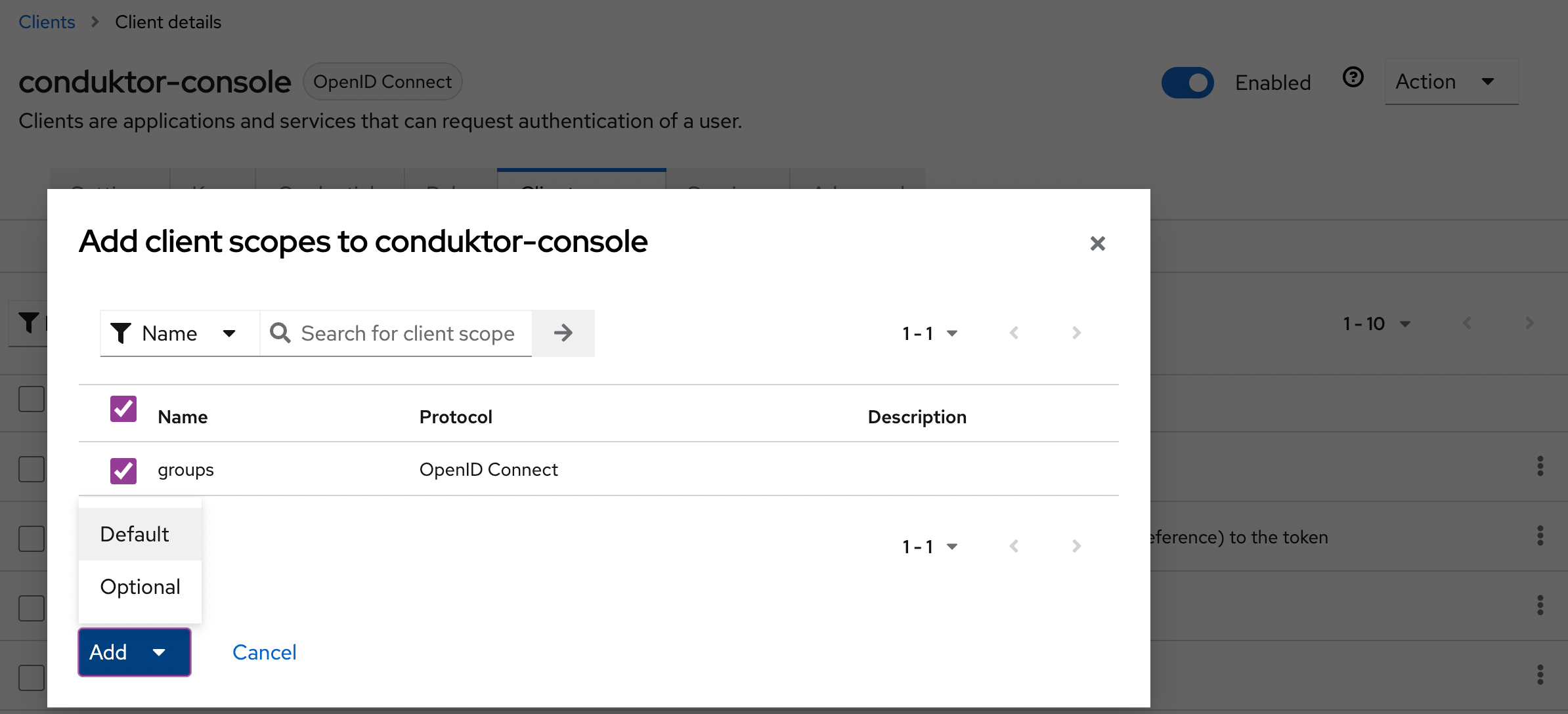
Then, you must set the property groups-claim to "groups" in the Console configuration file. Below is the full snippet for your configuration file:
- YAML File
- Environment Variables
sso:
oauth2:
- name: "keycloak"
client-id: "<client ID>"
client-secret: "<client secret>"
groups-claim: "groups"
openid:
issuer: "http://<Keycloak host>:<Keycloak port>/realms/<realm name>"
CDK_SSO_OAUTH2_0_NAME="keycloak"
CDK_SSO_OAUTH2_0_DEFAULT=true
CDK_SSO_OAUTH2_0_CLIENTID="<client ID>"
CDK_SSO_OAUTH2_0_CLIENTSECRET="<client secret>"
CDK_SSO_OAUTH2_0_GROUPSCLAIM="groups"
CDK_SSO_OAUTH2_0_OPENID_ISSUER="http://<Keycloak host>:<Keycloak port>/realms/<realm name>"
External Groups Mapping
Now that your configuration is finished, you can setup the mapping between Keycloak and Console groups. That way, when a user logs in, they will be automatically added to the corresponding Console groups, based on the groups they belong to in Keycloak.
The value you need to put as an external group is the name of the Keycloak group.
If you've selected Full group path in the mapper details of the scope, you will need to use the full path instead of the name of the group.